Executive Summary: The Silent Compromise of Knowledge Bases
In the rapid evolution of the “AI-Native” application stack (2025–2026), the focus of security engineers has largely been captivated by novel attack vectors: Prompt Injection, Jailbreaking, and Model Inversion. However, as platforms like Dify mature into enterprise-grade RAG (Retrieval-Augmented Generation) orchestrators, we are witnessing a resurgence of classic web vulnerabilities—specifically IDOR (असुरक्षित प्रत्यक्ष वस्तु संदर्भ)—manifesting in the new “Knowledge Supply Chain.”
This article provides an exhaustive technical analysis of the Dify IDOR vulnerability affecting Remote Data Source Bindings (referenced in GitHub Issue #31839). We will dissect the architectural flaw that allows unprivileged users to manipulate the “brain” of an AI agent, analyze the broader pattern of access control failures in the ecosystem (referencing CVE-2025-63387 और CVE-2025-58747), and demonstrate how the next generation of automated penetration testing must evolve to catch these logic gaps.
The Architecture of Vulnerability: How Dify Manages Knowledge
To understand the exploit, one must first understand the target. Dify operates on a multi-tenant architecture where a single instance (or cluster) serves multiple “Workspaces” (Tenants). Within these tenants, the core value proposition is the ability to bind unstructured data—Notion pages, Google Drive docs, Web Scrapes—to an LLM via a Vector Database.
The DataSourceOauthBinding is the critical linkage entity. It stores:
- The Provider: (e.g., Notion, GitHub).
- The OAuth Token: (Encrypted access to the external data).
- The Scope: (Which pages/repos are accessible).
- The Binding ID: A unique identifier (often a UUID or Integer) in the Postgres database.
In a secure design, every query to this table must be scoped by tenant_id. The Dify IDOR vulnerability arises when this scoping is missed in the API endpoint handling updates (PATCH/PUT) or deletions (DELETE).
Technical Autopsy: The Data Source Binding IDOR
The vulnerability resides in the API endpoints responsible for enabling, disabling, or refreshing these data source bindings.
The Flawed Logic (Reconstruction)
Let’s reconstruct the vulnerable code path typical of this specific IDOR, based on the findings in Dify GitHub Issue #31839. The backend framework (Python/Flask/SQLAlchemy) exposes an endpoint to update the status of a binding.
Python
`# VULNERABLE ENDPOINT LOGIC (Reconstruction) @api.route(‘/console/api/data-source/bindings/<binding_id>’, methods=[‘PATCH’]) @login_required def update_data_source_binding(binding_id): “”” Updates the enabled/disabled state of a data source. “”” # 1. Input Validation (Syntactic) – PASS parser = reqparse.RequestParser() parser.add_argument(‘enabled’, type=bool, required=True) args = parser.parse_args()
# 2. Database Query (The Security Flaw)
# The developer queries by ID only, assuming the UUID is entropy enough
# or relying on implicit trust.
binding = db.session.query(DataSourceOauthBinding).filter(
DataSourceOauthBinding.id == binding_id
).first()
if not binding:
raise NotFound("Binding not found")
# 3. Logic Execution
# CRITICAL FAILURE: No check to see if binding.tenant_id == current_user.tenant_id
binding.enabled = args['enabled']
binding.updated_at = datetime.utcnow()
db.session.commit()
return jsonify({"result": "success"}), 200`
The Exploit Chain
For a Red Teamer or a malicious insider, the exploitation steps are methodical:
Phase 1: Reconnaissance & ID Enumeration
The attacker logs into their own Dify account and inspects the network traffic when toggling a Notion integration.
- Request:
PATCH /console/api/data-source/bindings/550e8400-e29b-41d4-a716-446655440000 - Observation: The ID format. If it is a UUID, the attack requires an ID leak (Side-Channel or Information Disclosure). If it is a sequential Integer (common in older migrations), it is trivially enumerable.
Note: Even with UUIDs, IDOR is possible if other endpoints (like GET /console/api/public/stats or error messages) leak object references.
Phase 2: Cross-Tenant Manipulation
The attacker sends a crafted cURL request using their own valid JWT (Authorization Bearer token) but targeting a victim’s binding_id.
Bash
curl -X PATCH "<https://api.dify.target/console/api/data-source/bindings/TARGET_BINDING_UUID>" \\ -H "Authorization: Bearer <ATTACKER_JWT>" \\ -H "Content-Type: application/json" \\ -d '{"enabled": false}'
Phase 3: The Impact – RAG Denial of Service (DoS)
The server processes the request. Since the database query found the ID, and the code didn’t check the Tenant Owner, the binding is disabled.
- Result: The victim’s AI Agent, which relies on that Notion page for its Knowledge Base, suddenly starts hallucinating or replying “I don’t know,” as its context retrieval pipeline has been severed remote-control.
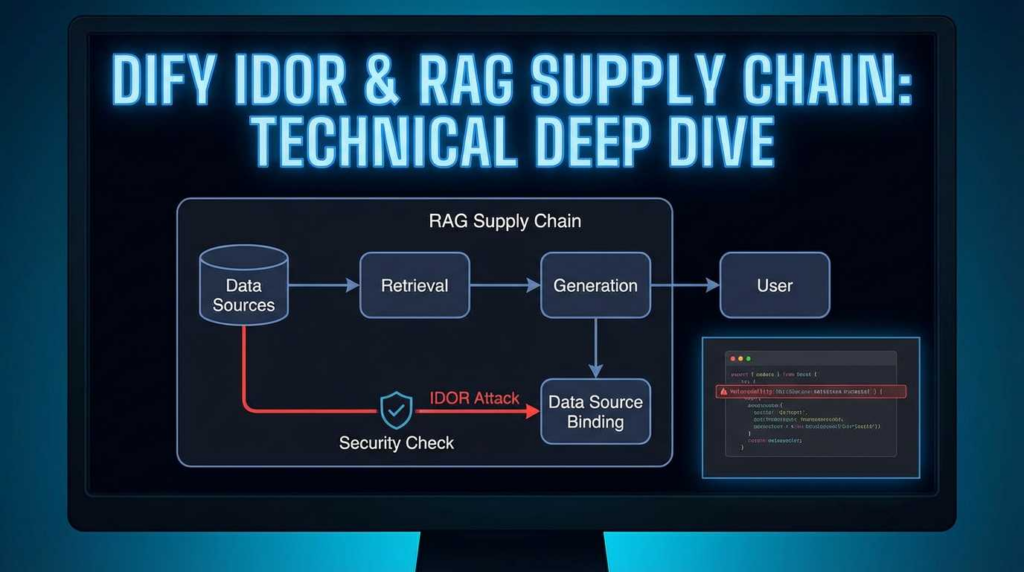
The Wider CVE Landscape: A Pattern of Broken Access Control
This IDOR is not an isolated incident. It fits into a broader pattern of “Broken Access Control” (OWASP LLM01) plaguing the Dify ecosystem in late 2025. Analyzing recent CVEs reveals a systemic issue where the speed of feature delivery (Agents, Workflows, MCP) outpaced the implementation of rigid RBAC (Role-Based Access Control).
| CVE ID / Issue | अवयव | Vulnerability Logic | Severity |
|---|---|---|---|
| GitHub Issue #31839 | Data Source Binding | IDOR. Missing tenant_id scope in ORM queries allowing remote manipulation of RAG sources. | High |
| CVE-2025-63387 | System Features | Insecure Permissions. The /console/api/system-features endpoint allowed unauthenticated users to read system configs. This implies a “Default Allow” mindset in routing. | Medium/High |
| CVE-2025-58747 | MCP OAuth | XSS & RCE. The Model Context Protocol (MCP) implementation trusted remote server URLs blindly (window.open), allowing XSS. | Critical |
| CVE-2024-11821 | Model Config | Access Control. Unprivileged users could alter chatbot model configurations via /console/api/apps/{chatbot-id}/model-config. | High |
Analysis:
The recurrence of CVE-2025-63387 and CVE-2024-11821 highlights a struggle with Object-Level Authorization. The platform validates “Is the user logged in?” (Authentication) but fails to rigorously validate “Is this user the owner of this specific row in the database?” (Authorization).
Why Traditional DAST Fails: The Logic Gap
Security Engineers often ask: “Why didn’t Nessus, Burp Suite Pro, or Zap catch this?”
The answer lies in the nature of Logic Bugs.
- HTTP Status Codes are Deceptive: To a scanner, a
200 OKfrom a PATCH request looks like a success. The scanner doesn’t know that User A shouldn’t have been able to modify User B’s object. - Context Blindness: Scanners do not understand the concept of “Tenants” or “Bindings.” They see opaque strings.
- State Dependency: Testing IDOR requires a complex setup: Create User A, Create User B, Create Resource A, Login as B, Try to Access Resource A. Standard scans are usually single-user sessions.
The Solution: AI-Native Automated Pentesting
This is where the paradigm shifts from “Scanning” to “Reasoning.” To catch a Dify IDOR, you need an engine that understands the semantics of the API.
This is the core engineering philosophy behind पेनलिजेंट.ai.
How Penligent Detects Logic Flaws
Unlike regex-based scanners, Penligent utilizes Large Language Models (LLMs) configured as autonomous security agents.
- Semantic API Mapping: Penligent reads the Swagger/OpenAPI spec of Dify and understands that
/bindings/{id}implies a resource modification. It infers that{id}is a sensitive reference. - Multi-Actor Orchestration: The platform spins up two distinct persona containers:
- Attacker Agent (User A)
- Victim Agent (User B)
- Context-Aware Fuzzing: The Attacker Agent explicitly attempts to access the Victim’s resources.
- Agent Reasoning: “I see a
binding_idin User B’s traffic. I will attempt to PATCH this ID using User A’s session token.” - Verdict Analysis: If the API returns
200 OKand the database state changes, Penligent flags a Confirmed IDOR.
- Agent Reasoning: “I see a
Integration into DevSecOps:
YAML
`# .gitlab-ci.yml example stages:
- security-test
penligent-check: stage: security-test script: – penligent-cli scan –target https://staging.dify-instance.com –mode logic-deep-dive only: – master`
By integrating tools like Penligent, security teams move from “Compliance Scanning” to “Adversarial Simulation,” effectively catching the logic flaws that CVE-2025-63387 and the Data Source IDOR represent.
Remediation: Implementing Row-Level Security
For developers and security engineers patching Dify (or similar AI platforms), the fix involves enforcing strict ownership checks at the Data Access Layer (DAL).
The Secure Pattern (Python/SQLAlchemy):
Python
`# SECURE IMPLEMENTATION @api.route(‘/console/api/data-source/bindings/<binding_id>’, methods=[‘PATCH’]) @login_required def update_data_source_binding_secure(binding_id): # 1. Context Extraction # Always derive tenant_id from the trusted session token, NEVER from client input current_tenant_id = current_user.current_tenant_id
# 2. Scoped Query (The Fix)
# We NEVER query by ID alone. We always AND it with the tenant_id.
binding = db.session.query(DataSourceOauthBinding).filter(
DataSourceOauthBinding.id == binding_id,
DataSourceOauthBinding.tenant_id == current_tenant_id
).first()
# 3. Secure Failure Mode
if not binding:
# Return 404 Not Found to prevent ID enumeration.
# Do NOT return 403 Forbidden, as that leaks the existence of the ID to attackers.
abort(404)
# 4. Logic Execution
binding.enabled = request.json['enabled']
db.session.commit()
return jsonify({"status": "updated"})`
Key Takeaways for the Fix:
- Tenant Context is King: Every query must include
tenant_id. - Silence the Errors: उपयोग
404 Not Foundfor unauthorized access to resources, not403. This prevents attackers from mapping out your database IDs (Oracle Attack). - UUIDs are not Security: Using UUIDs helps prevent sequential enumeration, but it does not prevent IDOR if the ID is leaked. Access Control is the only true defense.
The Future of AI AppSec
The Dify IDOR vulnerability serves as a critical case study for the industry. As we rush to build “Agentic” futures where AI performs actions on our behalf, the underlying web security foundations cannot be ignored. A compromised Data Source Binding doesn’t just mean data loss; in the age of RAG, it means reality distortion for the AI model.
Security engineers must adapt. We must look beyond simple injection attacks and focus on the complex logical relationships between Tenants, Agents, and Knowledge Bases. Whether through rigorous code review or the adoption of AI-native testing platforms like Penligent, securing the “Knowledge Layer” is the defining challenge of 2026.
References & Further Reading:
- GitHub Issue #31839: Dify DataSourceOauthBinding IDOR Vulnerability
- GitHub Advisory: Dify System Features Permissions (CVE-2025-63387)
- NVD Detail: CVE-2025-58747 (MCP OAuth XSS)
- OWASP Top 10 for LLM Applications: IDOR & Data Poisoning
- Penligent Blog: Why Traditional DAST Misses Logic Vulnerabilities