Spring Security protects Java applications by wrapping every HTTP request in a structured security pipeline, using a filter-chain that handles authentication, authorization, and multiple layers of defense such as CSRF, CORS, session management, and token validation. This architecture ensures that only authenticated and authorized users access resources, whether your application is a monolithic web-app, a REST API, or a microservices backend.
In effect, Spring Security becomes your application’s “guard rails,” so you don’t have to build a security system from scratch — but rather configure, extend, and harden a proven, community-trusted foundation.
The Core Engine: Request Flow & Security Filter Chain
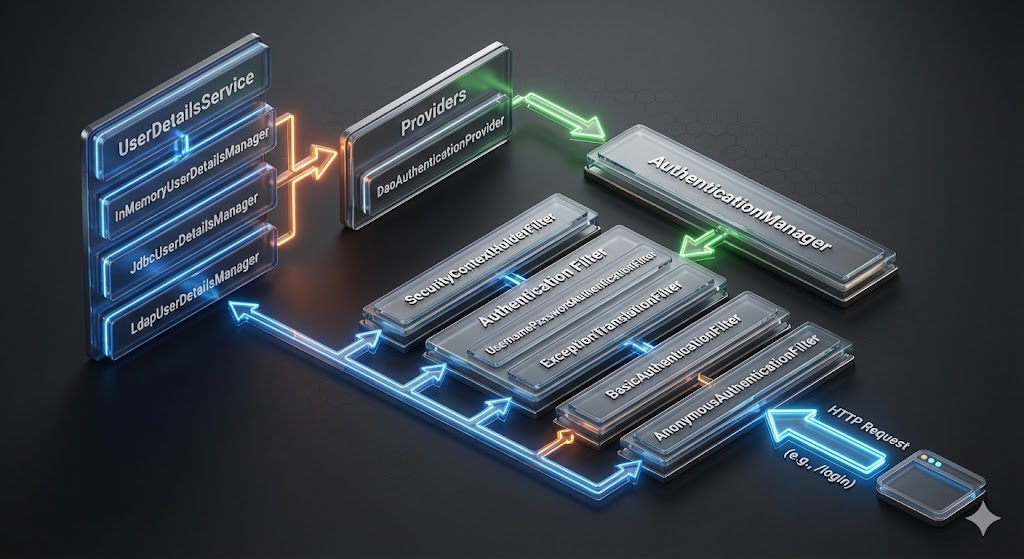
Spring Security’s backbone is the Servlet Filter mechanism. Every incoming HTTP request passes through the SecurityFilterChain, a sequence of filters each responsible for a distinct security concern. This design cleanly separates security from business logic, and enables extensibility: you can inject custom filters or authentication providers without touching controllers or services.
Request Lifecycle in Spring Security
| Phase | Component / Filter | उद्देश्य |
|---|---|---|
| 1 | SecurityContextPersistenceFilter | Load existing SecurityContext (if session-based) or create blank context |
| 2 | Authentication Filter (e.g. UsernamePasswordAuthenticationFilter, BearerTokenAuthenticationFilter etc.) | Attempt authentication based on credentials (form login, token, etc.) |
| 3 | SessionManagementFilter / concurrency control | Handle session fixation, session concurrency, or stateless policy |
| 4 | AuthorizationFilter / FilterSecurityInterceptor | Enforce URL- or method-level access control (roles/permissions) |
| 5 | CSRF / CORS / Header-writing Filters | Enforce cross-site request protections, security headers |
| 6 | Request reaches Controller / Business Logic | Security context now holds an authenticated, authorized principal |
Because Spring Boot / Spring Security wires this chain automatically when you add the correct dependencies, many security concerns are instantly covered. Yet — you still have full control to extend, replace or reorder parts as needed.
Authentication Mechanisms: From Form Login to JWT & OAuth2
One of Spring Security’s core strengths is its flexibility: it supports a variety of authentication strategies, making it suitable for traditional web apps, mobile backends, single-page apps (SPAs), and microservices.
Traditional Session-Based Login
For web applications, form-based login (or HTTP Basic) remains a valid default:
java
http .authorizeHttpRequests(auth -> auth .requestMatchers("/public/**").permitAll() .anyRequest().authenticated() ) .formLogin(Customizer.withDefaults());
Upon successful login, Spring Security stores authentication in an HTTP session, and wraps subsequent requests with SecurityContext automatically. This method works well for server-rendered apps where cookies and sessions are acceptable.
Stateless JWT Authentication for APIs
Modern architecture — especially REST APIs, SPAs, or microservices — often requires stateless, token-based authentication. Spring Security supports this cleanly via its OAuth2 Resource Server module and built-in JWT validation. Home+1
A minimalist configuration looks like this:
java
@Configuration @EnableWebSecurity public class JwtSecurityConfig {@Bean public SecurityFilterChain securityFilterChain(HttpSecurity http) throws Exception { http .csrf(csrf -> csrf.disable()) .sessionManagement(sess -> sess.sessionCreationPolicy(SessionCreationPolicy.STATELESS)) .authorizeHttpRequests(auth -> auth .requestMatchers("/api/auth/**", "/api/public/**").permitAll() .anyRequest().authenticated() ) .oauth2ResourceServer(oauth2 -> oauth2.jwt(Customizer.withDefaults()));return http.build(); } }
Spring Boot automatically configures the JwtDecoder, validates JWT signature, iss (issuer), exp / nbf (timestamps), and maps scopes to authorities. docs.enterprise.spring.io+1
That makes secure API protection quick to deploy, with minimal boilerplate, while preserving security best practices.

OAuth2 / OpenID Connect for SSO & Third-Party Login
If your application needs single-sign-on (SSO), social login (Google, GitHub, etc.), or delegated identity via an external authorization server, Spring Security’s OAuth2 Client support makes integration straightforward. You can obtain access tokens, refresh tokens, and user identity via OIDC — and then rely on Resource Server behavior for your backend APIs.
This flexibility lets you unify user identity across web, mobile, and third-party auth providers — ideal for large-scale, distributed apps.
Authorization & Access Control: Who Can Do What
Authentication proves identity. Authorization determines permissions. Spring Security supports fine-grained control at both URL-level and method-level.
- URL-based access control: simple role-based restrictions on endpoints.
- Method-level security: by enabling annotations like
@PreAuthorize,@Secured,@PostAuthorize, you can enforce permissions directly in service or controller methods. - Attribute-based or claim-based access control: especially when using JWTs — you can inspect claims (e.g. tenant, user attributes, scopes) to enforce dynamic permissions.
This layered approach (URL → method → business logic) gives you full control over who can access what, under which conditions.
Built-in Protections & Security Hardening Features
Spring Security provides more than just authentication and authorization — it includes many mechanisms to defend against common web attacks and misconfiguration. Among them:
- CSRF protection — enabled by default for session-based flows. Disable only if you fully control the client (e.g. SPA with JWT).
- CORS configuration — crucial for modern frontends interacting with APIs.
- Secure password storage — supports strong hashing algorithms like BCrypt, PBKDF2, Argon2. Avoid weak hashes (MD5, SHA-1). Studies show misuse of hashing is a common security anti-pattern. arXiv+1
- Session management & session fixation protection — prevents session hijacking and enforces concurrency limits.
- HTTP security headers — HSTS, frame options, XSS protection, content security, etc.
But defaults aren’t magic: security depends heavily on how you configure and test your setup. Empirical studies reveal multiple misconfiguration anti-patterns — e.g. disabling CSRF, using weak password hashing — in real Spring apps, leading to serious vulnerabilities. arXiv
Hence, rigorous security auditing, code review, dependency updates, and automated testing are critical.
Common Pitfalls & How to Avoid Them
Even a mature framework like Spring Security can be misused — especially when developers mix different auth modes, override default configs, or overlook edge cases. Here are some recurring issues observed in the community:
| Issue / Mistake | Consequence | How to Mitigate |
|---|---|---|
| Mixing session-based login and stateless JWT without separate filter chains | Conflicts, unexpected behavior, security holes | Use separate SecurityFilterChain beans with distinct request matchers for different auth schemes (Reddit) |
| Disabling CSRF without proper alternative protections (e.g. for forms) | Vulnerable to CSRF attacks | Only disable CSRF for stateless APIs, ensure tokens or other protections for stateful scenarios |
| Using weak password hashing (MD5, SHA-1) or storing plaintext passwords | Easy to break if data leaks | Always use BCryptPasswordEncoder, Argon2, or similar strong hashing + salt |
| Incorrect JWT configuration (missing iss, aud validation, wrong key rotation) | Tokens can be forged or remain valid beyond intended lifetime | Use official OAuth2 Resource Server config; enable signature, issuer, audience validation, and key rotation (घर) |
| Insufficient testing (unit tests, integration tests, token expiration, revocation, error paths) | Bugs or security holes slip into production | Write automated tests covering authentication, failure paths, token handling, logout, refresh logic. Research shows many real-world apps lack these tests. (arXiv) |
As one developer put it (in a community discussion): “Every Spring Security tutorial leads to deprecated code … even updated methods are already marked for removal.” Reddit
That points to another risk: you must stay current with Spring Security versions and migrate configurations accordingly.
Example: Secure REST API with JWT + Resource Server
Here’s a minimal example of a Spring Boot REST API secured via JWT in stateless mode.
java
@Configuration @EnableWebSecurity public class ApiSecurityConfig {@Bean public SecurityFilterChain securityFilterChain(HttpSecurity http) throws Exception { http .csrf(csrf -> csrf.disable()) .sessionManagement(sm -> sm.sessionCreationPolicy(SessionCreationPolicy.STATELESS)) .authorizeHttpRequests(auth -> auth .requestMatchers("/api/auth/**", "/api/public/**").permitAll() .anyRequest().authenticated() ) .oauth2ResourceServer(oauth2 -> oauth2.jwt(Customizer.withDefaults()));return http.build(); } }
And properties in application.yml:
java
spring: security: oauth2: resourceserver: jwt: issuer-uri: <https://idp.example.com> audiences: <https://your-api.example.com>
This setup ensures that:
- JWT signature, issuer (
iss), audience (aud), expiration (exp) are all validated automatically, following best practices for token-based security. Home+1 - No HTTP session is created (stateless), making the API scalable.
- You rely on standard modules; no custom filter classes or boilerplate authentication code required.
You can further customize by defining a custom JwtAuthenticationConverter to map claims → roles or authorities, or wrapping additional checks (Scopes, tenants, etc.).
Recommendations & Best Practices for Production Readiness
If you’re building real-world applications — especially public APIs, microservices, or services requiring penetration testing / vulnerability auditing — then treat Spring Security as a baseline, and layer on hardening, logging, monitoring, and testing.
- Use strong password hashing: prefer BCrypt or Argon2.
- Prefer stateless JWT / OAuth2 Resource Server for APIs — avoid session-based auth in microservices or distributed systems.
- Always validate JWTs properly — enforce signature verification,
issऔरaudclaims, expiration, and consider key rotation. - Separate filter chains if mixing auth methods — e.g. one for session-based web, one for JWT-based API.
- Enable CSRF for traditional forms; configure CORS for SPAs and external clients.
- Implement logging, monitoring, rate limiting, and alerting — unexpected auth failures or multiple failed logins should trigger alerts.
- Write automated tests (unit + integration) for authentication, authorization, token expiry, error paths, refresh & logout flows — many real-world apps omit this, increasing risk. arXiv+1
- Stay current with Spring Security versions — community feedback shows tutorials often become outdated, and misuse / deprecated APIs remain a pain. Reddit+1
Why Spring Security Remains the Go-To Security Framework in Java Ecosystem
Several factors contribute to Spring Security’s dominance in Java security:
- It’s feature-complete: authentication, authorization, CSRF, session management, token support, OAuth2, etc.
- Highly configurable and extensible — you can plug in custom filters, authentication providers, user stores, and security policies.
- Broad integration with Spring Boot / Spring ecosystem — minimal friction to add security to existing apps.
- Community mature and battle-tested — lots of community guides, open-source projects, and real-world usage across industries.
- Standardized security baseline, which benefits automated testing, vulnerability scanning, and penetration testing tools.
For teams working on penetration testing, automated vulnerability scanning, API security tools, or AI-driven security platforms — using Spring Security means you have a predictable security baseline to analyze, test, and audit against. That predictability is valuable when building security tooling or embedding security into CI/CD pipelines.
निष्कर्ष
Spring Security is not magic — but it is a powerful, battle-tested foundation for securing Java web applications, APIs, and microservices. By default, it covers many common web security needs; when configured properly, it protects against CSRF, enforces authentication and authorization, ensures secure password storage, validates JWTs, and supports modern identity protocols like OAuth2 / OpenID Connect.
However, the real strength lies in how developers configure and harden it: adopting strong password hashing, stateless JWT for APIs, precise authorization rules, secure token validation, and comprehensive testing and monitoring.
For developers and security engineers — especially those building or testing real-world systems, or building security tools — I strongly recommend treating Spring Security as the baseline security layer, and building further: rigorous configuration, secure defaults, automated tests, and regular audits.
With this approach, you get a robust, flexible, maintainable, and secure foundation — and you avoid the common pitfalls many Spring-based applications fall into.


