In the modern cyber offense and defense landscape, Vertical vs Horizontal privilege escalation is far more than a technical label in penetration testing reports; it represents a deeper security challenge that spans software architecture, identity management, and access control. Once attackers break privilege boundaries—whether vertically or horizontally—they can bypass isolation mechanisms, gain access to core repositories of sensitive data, and even acquire the ability to alter critical system parameters. For professionals engaged in penetration testing, automated vulnerability discovery, and intelligent security tooling, understanding the intrinsic differences and real-world threats of these two attack modes is essential to maintaining an effective defense in a rapidly evolving threat environment.

What is Privilege Escalation?
Privilege escalation refers to an attacker gaining access or capabilities beyond the scope of their legitimate permissions. This escalation can be vertical—moving upward into a higher privilege tier—or horizontal—expanding laterally to access resources and data owned by other accounts at the same privilege level.
The Key Differences Between Vertical and Horizontal Privilege Escalation
Vertical Privilege Escalation
Vertical privilege escalation occurs when an attacker moves from a low-privilege account—such as a regular user, guest, or test account—into a higher-privilege tier like system administrator, root, or superuser. This shift has serious consequences because it grants direct control over the most critical aspects of the system: modifying security settings, accessing and exporting sensitive databases, managing or deleting user accounts, and executing commands that are normally reserved for privileged roles.
In many cases, the entry point is an overlooked high-privilege endpoint or an inadequately protected admin panel, which leaves low-privilege users with a path to escalate. It can also be the result of operating system–level flaws, such as kernel buffer overflow vulnerabilities or privilege bypass issues in outdated versions. Exploiting such flaws allows attackers to leap past standard security boundaries in one move.
# Exploiting a local privilege escalation vulnerability (example: Linux Dirty Pipe CVE)
searchsploit dirty pipe
gcc exploit.c -o exploit
./exploit
# Verify elevated privilegeswhoami
# Expected output: root
This is a simplified demonstration of how an attacker, starting from a low-privilege shell, might exploit a known local privilege escalation vulnerability (such as Dirty Pipe) to gain root permissions.
Horizontal Privilege Escalation
Horizontal privilege escalation happens entirely within the same privilege level. The attacker does not change their account’s role but gains access to data or functionality belonging to other users with equivalent privileges. This often exploits weaknesses in authorization logic—such as backend APIs failing to check on every request whether the user is authorized to access the resource—or flaws in session token generation and management that allow impersonation through token swapping or forgery.
In penetration testing, these issues often appear as predictable or modifiable object IDs. For example, on an e-commerce platform, if the order detail URL is https://shop.com/order?id=1001, simply modifying the id parameter may expose other users’ order information.
# Original request (current user viewing own order)
GET /order?id=1001 HTTP/1.1
Host: shop.com
Cookie: session=abc123
# Modified request (attempting to access another user's order)GET /order?id=1002 HTTP/1.1
Host: shop.com
Cookie: session=abc123
# If the server returns another user's order details, a horizontal privilege escalation vulnerability exists.
This demonstrates an attacker accessing another user’s data by simply altering a parameter in the request, without any change in privilege level.
Vertical vs Horizontal Privilege Escalation
| Type | English Description | Example Scenario |
|---|---|---|
| Vertical | Escalate from low to high privilege level for broader control | A regular user exploiting a flaw to become a system administrator |
| Horizontal | Access peer account data/functions within the same privilege level | A user modifying an ID to view another user’s private files |
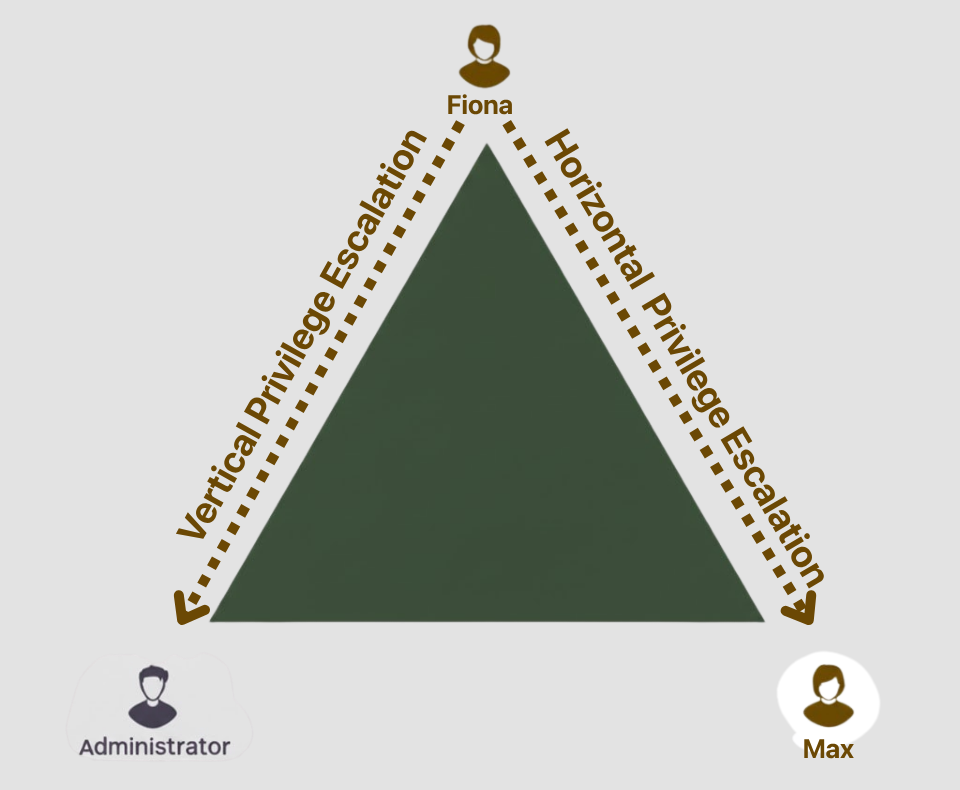
Common Techniques and Scenarios for Discovering Vertical and Horizontal Vulnerabilities
When hunting for vertical privilege escalation, testers often focus on uncovering exposed admin endpoints, misconfigured high-privilege APIs, or unpatched local escalation flaws in the operating system. In contrast, horizontal privilege escalation testing centers on authorization logic flaws, exposed predictable object IDs, and improper session management.
In one penetration test against a financial platform, researchers discovered that low-privilege account holders could directly view other customers’ transaction data—a textbook horizontal vulnerability. Further investigation revealed that the platform’s admin panel could be accessed without additional authentication—a classic vertical escalation case. The combination of both types of privilege escalation escalated the potential impact significantly.
Leveraging Intelligent Tools for Vertical and Horizontal Vulnerability Discovery
Traditionally, detecting these vulnerabilities required juggling multiple tools manually and correlating the results yourself. Intelligent penetration testing platforms like Penligent have revolutionized this process. By issuing a natural language command, Penligent automatically selects and runs suitable tools—such as SQLmap or Nuclei—validates the vulnerabilities, filters out false positives, and generates a prioritized remediation plan. This enables near real-time vertical and horizontal escalation detection, transforming how security teams identify and handle critical privilege escalation risks.
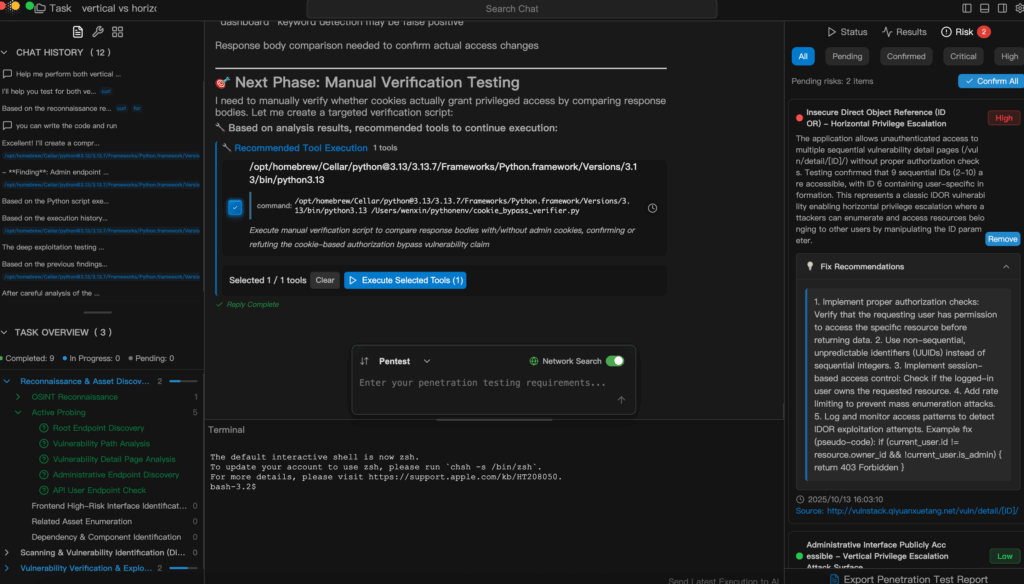
Effective Measures to Address Vertical and Horizontal Privilege Escalation
Defending against these two categories still relies on foundational strategies: enforcing the principle of least privilege, implementing strict and consistent access controls, and maintaining continuous monitoring and auditing. However, as modern systems evolve rapidly with frequent feature updates, the attack surface also changes.
The most effective defense combines proactive vulnerability discovery with verified remediation. Platforms like Penligent not only allow security teams to find and validate vertical and horizontal escalation paths early but also to prioritize fixes and coordinate remediation collaboratively. By understanding that attack paths have both height and breadth, defenders can adopt a multi-layered, multidirectional defensive architecture.


