Most teams think of an Information Disclosure Statement as paperwork —
a compliance checkbox after the breach is already public.
But in practice, it’s also the most structured window into how your systems actually failed.
The problem is: disclosure happens late, fragmented, and reactive.
Logs are scattered across WAFs, API gateways, and build servers.
By the time the statement is assembled, the incident has evolved, and your visibility is gone.
Penligent changes that.
From static reporting to living evidence
Penligent treats disclosure not as an administrative step, but as a real-time security artifact.
Instead of waiting for analysts to summarize, it listens, reconstructs, and compiles.
A natural-language request is enough to start:
"Generate an Information Disclosure Statement for the login endpoint exposure.
Include timeline, affected assets, and remediation plan."
Under the hood, the system doesn’t just fill a template.
It pulls correlated evidence — WAF logs, API traces, and error dumps —
and rebuilds the story of the breach from signal patterns.
def build_information_disclosure(event):
logs = penligent.collect(["WAF", "DB", "App"])
scope = analyzer.assess(logs)
timeline = penligent.sequence(logs)
report = penligent.compose(
title="Information Disclosure Statement",
sections=["Summary", "Evidence", "Impact", "Remediation"]
)
return report
It’s not automation for convenience.
It’s automation for clarity — an always-on memory of what went wrong, while it’s still fresh.
The value of context
Most incident statements are linear: what happened, who was affected, when it was fixed.
Penligent’s version adds dimension.
It cross-references vulnerabilities, checks CVE relevance, and ranks severity based on environmental context.
You don’t just get:
“Stack trace leaked internal class path.”
You get:
“Stack trace indicates framework version exposure; linked to CVE-2025-24085;
potential lateral impact via auth microservice.”
That’s no longer a report — it’s operational intelligence.
Reports that think for themselves
What makes a disclosure meaningful isn’t format, it’s judgment.
Penligent’s reasoning layer adds that judgment automatically —
weighing whether a finding is significant, repeatable, or regulatory-relevant.
It translates scanner noise into a concise narrative:
{
"incident_id": "INC-2025-0784",
"summary": "Exposure of debug API logs containing PII",
"root_cause": "Verbose logging during beta rollout",
"confidence": 0.95,
"impact": "Moderate, 162 users affected",
"next_steps": ["Sanitize logs", "Rotate tokens", "Notify users within 72h"]
}
The structure looks like compliance, but the intent is operational —
to shorten the time from detection to disclosure,
and from disclosure to defense.
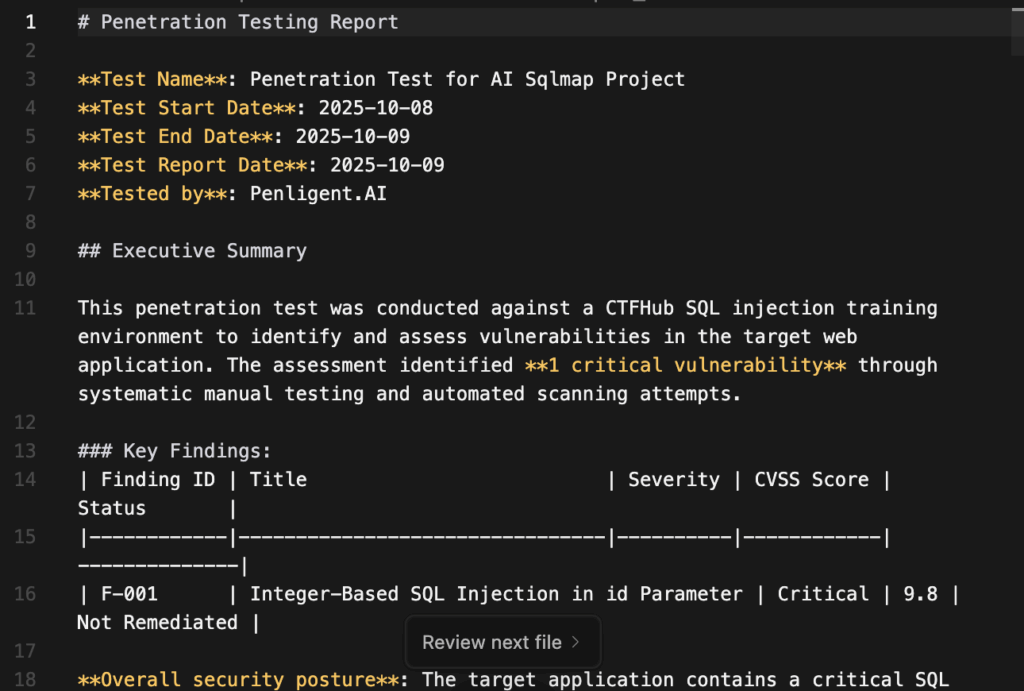
Why this matters now
Security teams used to separate testing and reporting.
One found problems; the other explained them.
In a world of continuous deployment and AI-assisted exploits, that separation is no longer viable.
Penligent bridges those two realities —
turning disclosure statements into dynamic briefings that evolve as new evidence arrives.
You don’t need another dashboard.
You need a system that knows when a log line turns into a liability,
and when a liability turns into a story worth reporting.
Compliance as a side effect of good security
Penligent’s Information Disclosure Statement isn’t built for auditors first — it’s built for defenders.
Regulations like GDPR or CCPA are baked in as metadata, not as afterthoughts.
When the system generates a disclosure, it auto-tags jurisdictional obligations,
suggests who must be notified,
and formats the output in a legally acceptable structure —
but the substance stays technical, precise, and actionable.
Compliance doesn’t have to be paperwork.
It can be an extension of situational awareness.
The bigger shift
Information disclosure used to mark the end of an incident.
Now, it’s the start of the next layer of learning.
Penligent reframes it as an adaptive cycle:
detect → analyze → disclose → defend.
Every report strengthens the model’s context for future threats.
Every disclosure is not just an apology — it’s an update to collective defense.


