In the legacy view of cybersecurity, penetration testing was often romanticized as an art form—a manual, intuitive process performed by a “hoodie-wearing” expert acting on a hunch.
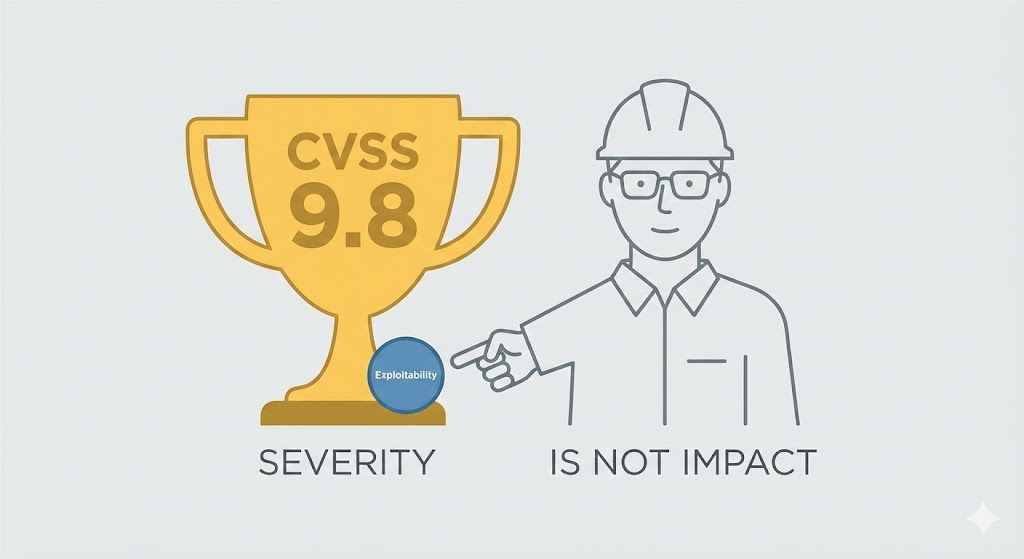
But for the modern security engineer, what is penetration testing? It is not magic. It is a rigorous engineering discipline. It is the practice of subjecting a system to a controlled, adversarial event to scientifically verify risk. Unlike vulnerability scanning, which merely identifies potential flaws, penetration testing exploits them to prove a path to critical assets.
As we move through 2025 and into 2026, the definition is evolving again. We are transitioning from the era of “Human-Driven” testing to “Agentic-Driven” validation, where AI systems don’t just scan—they reason, plan, and execute attacks.
From Vulnerability Assessment to Adversarial Emulation
To understand the core of the discipline, we must distinguish it from its noisier cousin: Vulnerability Management.
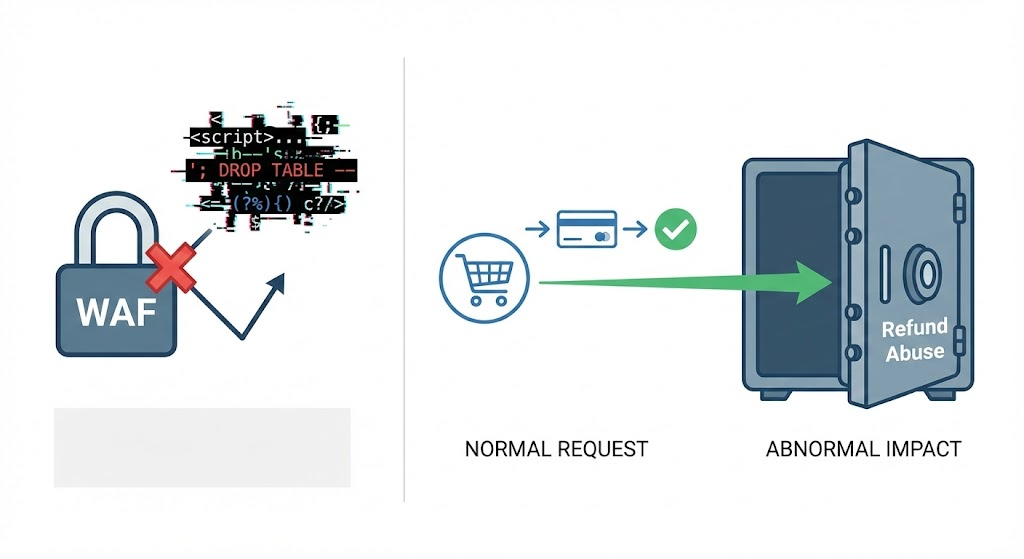
- Vulnerability Assessment (VA): A breadth-first search. It asks, “Is the door open?” It relies on version matching (e.g., “Apache 2.4.49 is vulnerable to Path Traversal”). It produces lists, often filled with false positives.
- Penetration Testing (Pentesting): A depth-first search. It asks, “Can I walk through that door, pivot to the internal network, and dump the database?” It relies on 체인 취약점.
The Modern Pentesting Lifecycle (PTES Updated)
동안 Pre-engagement Interactions 그리고 Reporting phases remain standard, the technical core has shifted significantly with the introduction of AI and automation.
| 단계 | Traditional Manual Actions | Modern Agentic / AI-Enhanced Actions |
|---|---|---|
| Intelligence Gathering (Recon) | whois, nslookup, manually browsing LinkedIn for employee names. | Autonomous OSINT: AI agents scraping GitHub commits for leaked API keys, mapping attack surfaces via Subdomain Takeover probability scoring. |
| Threat Modeling | Whiteboarding diagrams, static analysis. | Dynamic Graphing: Real-time visualization of potential attack paths based on current infrastructure state (Infrastructure as Code analysis). |
| Vulnerability Analysis | Running Nessus/Burp, manually validating false positives. | 컨텍스트 인식 퍼징: LLMs generating custom payloads based on the specific tech stack (e.g., generating GraphQL queries specific to your schema). |
| 익스플로잇 | Manually compiling exploits from Exploit-DB, adjusting offsets. | Auto-Exploit Generation: Agents rewriting POCs on the fly to bypass WAFs or specific filter rules. |
| 익스플로잇 후 | Manual pivoting, setting up C2 channels. | Stealth Persistence: Automated clean-up and “living off the land” (LotL) techniques using authorized admin tools to maintain access. |
Technical Deep Dive: The Anatomy of a Modern Exploit
To truly answer “what is penetration testing,” we must look at the code level. A pentester does not just run a tool; they understand the underlying flaw.
Let’s analyze a high-impact vulnerability class that dominated late 2025: Insecure Deserialization in Server Components (modeled after CVE-2025-55182 / React2Shell).
In modern web applications (Next.js, React Server Components), data is often serialized to pass state between server and client. If the application blindly deserializes user-controlled data without type checking, a pentester can inject a malicious object.

The Vulnerability Pattern
A vulnerable endpoint might look like this (simplified for conceptual demonstration):
자바스크립트
`// Vulnerable Server Component (Conceptual) import { unserialize } from ‘legacy-serializer’;
export async function POST(request) { const body = await request.text();
// DANGER: Deserializing input directly from the user // “What is penetration testing” implies finding exactly this line. const state = unserialize(body);
return <UserProfile data={state} />; }`
The Pentester’s Approach (The Proof of Concept)
A scanner might miss this because it looks like standard traffic. A pentester, however, analyzes the serialization format. They would craft a payload that, when deserialized, instantiates a class or function present in the runtime environment (a “Gadget Chain”) to execute code.
Conceptual Exploit Logic (Python):
Python
`import requests import base64
Target: A vulnerable React Server Component endpoint
url = "https://vulnerable-app.com/api/user/state“
The “Gadget”: A serialized payload that triggers a shell command
In a real engagement, this would pop a calculator or callback to the tester.
This proves RCE (Remote Code Execution) without damaging data.
payload = { “유형“: “System.Process”, “command”: “cat /etc/passwd”, “args”: [] }
Encode for transport (simulating the proprietary format)
serialized_data = base64.b64encode(str(payload).encode()).decode()
headers = { “Content-Type”: “application/x-java-serialized-object”, # Example header “User-Agent”: “Pentest-Agent-v1.0” }
print(f”[*] Sending probe to {url}…”) try: response = requests.post(url, data=serialized_data, headers=headers, timeout=5) if “root:x:0:0” in response.text: print(“[!] VULNERABILITY CONFIRMED: RCE via Deserialization”) print(“[+] Evidence extracted successfully.”) else: print(“[-] Target does not appear vulnerable or WAF blocked the request.”) except Exception as e: print(f”[-] Error during testing: {e}”)`
Note: Real-world exploitation of CVE-2025-55182 requires deep knowledge of the Flight protocol and React’s internal fiber nodes, making it a prime example of why human expertise (or advanced AI) is needed over simple scanners.
The Shift to Agentic AI in Penetration Testing
The biggest shift in the industry right now is the move from 자동화 에 자율성.
Traditionally, “automated pentesting” was a marketing lie. It was usually just a scheduled vulnerability scan. However, with the rise of Large Language Models (LLMs) and Agentic frameworks, we are seeing the birth of Autonomous Penetration Testing.
Why “Human-Only” Scaling Fails
- Speed of Dev vs. Speed of Test: Developers push code 50 times a day. A human pentest happens once a year. The math doesn’t work.
- The Context Gap: External testers don’t know the business logic. They spend 3 days just learning what the app does.
- Cost: A high-quality manual test for a microservices architecture can cost upwards of $50,000 per engagement.
Enter Penligent: The AI Penetration Tester
다음과 같은 플랫폼이 여기에 해당합니다. Penligent.ai are changing the paradigm. Penligent doesn’t just run scripts; it utilizes AI agents that mimic the decision-making process of a human ethical hacker.
Unlike a scanner that blindly fires XSS payloads at every input, an AI agent understands the 컨텍스트.
- It reads the code: It analyzes the JavaScript to understand that
user_idis validated but주문_IDflows into a SQL query. - It reasons: “If I can bypass the login via the API, I should try that before testing the front-end form.”
- It validates: It proves the exploit is real, filtering out the noise that plagues traditional security teams.
By integrating an AI pentester into the CI/CD pipeline, organizations achieve “Continuous Penetration Testing”—ensuring that every commit is vetted by a virtual security engineer before it hits production.
Essential Tools for the Modern Engineer
To answer “what is penetration testing” fully, one must know the toolkit. It is no longer just Kali Linux.
- Burp Suite Pro: The gold standard for web traffic interception and manipulation.
- Metasploit Framework: For post-exploitation and known vulnerability verification.
- Caido: The modern, Rust-based alternative to Burp, gaining traction for its speed.
- Nuclei: A fast, template-based scanner that allows engineers to write their own vulnerability checks (YAML) rapidly.
- Penligent: For automating the logic-heavy parts of the test that traditional scanners miss.
Conclusion: The Future of Offensive Security
So, what is penetration testing today?
It is the proactive identification of “Unknown Unknowns.” It is the only way to answer the board of directors’ question: “Are we safe?” with empirical data rather than hopeful assumptions.
As infrastructure becomes more complex and development cycles shorten, the hybrid model—where AI Agents handle the continuous, massive-scale testing of logic and code, and Human Experts focus on complex threat modeling and high-severity exploit chaining—is the only viable path forward.
For the security engineer, this means evolving. It means moving beyond running scripts to engineering the agents that run the scripts.
Recommended Resources & References
To deepen your understanding of the methodologies and vulnerabilities discussed, we recommend the following authoritative sources:
- NIST Special Publication 800-115 – The Technical Guide to Information Security Testing and Assessment.
- OWASP Top 10 – 2025 Data Analysis – The standard awareness document for developers and web application security.
- MITRE ATT&CK Framework – A globally accessible knowledge base of adversary tactics and techniques.
- Penligent Blog: The Era of Agentic Red Teaming – A deep dive into how AI is reshaping offensive security operations.
- Penligent Research: Automating Business Logic Attacks – How to move beyond simple CVE scanning.


