Why this CVE matters more than “just another local EoP”
CVE-2026-21533 is described as improper privilege management in Windows Remote Desktop that allows an authorized attacker 에 elevate privileges locally. (NVD) That sounds tame until you place it where attackers actually use it:
- After initial access, when they land as a standard user and need to become 시스템 quickly.
- Before they touch noisy lateral movement, credential dumping, or domain operations.
- Alongside other “friction-removal” bugs (security feature bypasses) from the same patch cycle, which increase the odds that an initial foothold happens at all. (컴퓨터)
Microsoft and multiple security vendors report active exploitation. Rapid7 and Tenable list it as “Exploitation Detected,” and CISA added it to the 알려진 익스플로잇 취약점(KEV) catalog with a remediation due date. (Rapid7)
If you run Windows fleets where RDP components are present (even if RDP isn’t exposed to the internet), treat this as a post-compromise accelerant: it shortens the time between “one phished user” and “full local control.”
What’s confirmed publicly
Core description and severity
NVD’s description is concise: improper privilege management in Windows Remote Desktop enables local privilege escalation by an authorized attacker. (NVD)
NVD lists a CVSS v3.1 vector: AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H. In practical terms: local attack vector, low complexity, requires low privileges, no user interaction, and high impact to confidentiality/integrity/availability once exploited. (NVD)
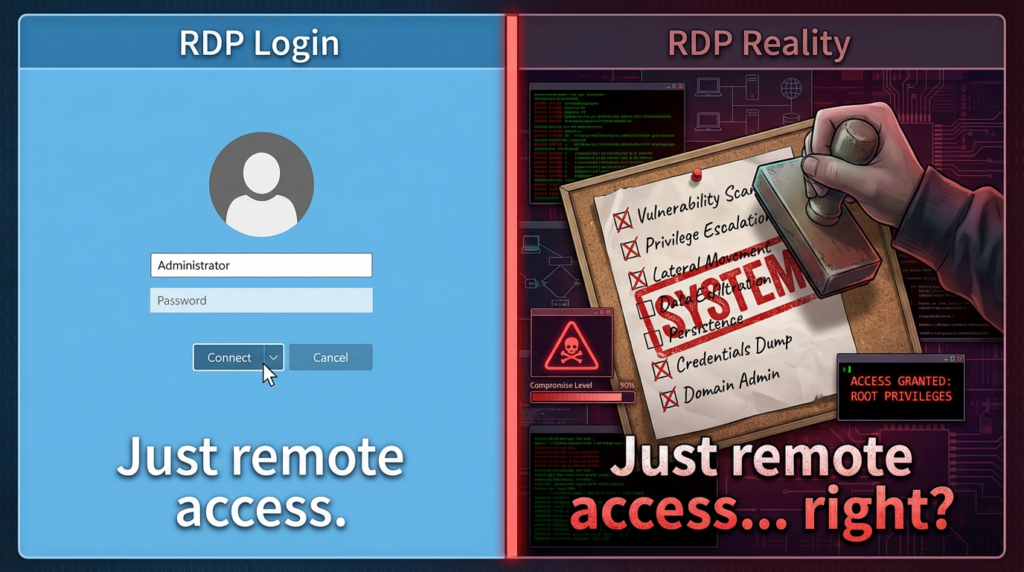
Active exploitation and KEV deadline
NVD explicitly flags that the CVE is in CISA’s KEV catalog, with:
- Date Added: 2026-02-10
- Due Date: 2026-03-03
- Required Action: apply mitigations per vendor instructions or discontinue use if unavailable (NVD)
That KEV “due date” is not a suggestion; it’s the cleanest external justification you can use to defend emergency change windows.
What’s been reported about exploitation mechanics (limited but useful)
Public reporting includes a high-signal detail from CrowdStrike’s Adam Meyers quoted by BleepingComputer: the exploit binary modifies a service configuration key and replaces it with an attacker-controlled key, enabling privilege escalation that could be used to add a new user to the Administrators group. (컴퓨터)
Important nuance: this is not a full technical write-up, and you should assume critical details remain private. But that single sentence tells defenders where to look: service configuration tampering 그리고 local admin group changes.
The “highest-click” search terms around this CVE
You asked for the click-driving phrases. I can’t see Google Search Console CTR data from here, but you can reliably infer what attracts clicks by looking at the repeated headline language across top-ranking coverage—because those publishers optimize for the same curiosity + urgency loop.
Across major coverage and patch roundups, the phrases that most consistently anchor the story are:
- “actively exploited” / “zero-day” (urgency + legitimacy) (컴퓨터)
- “Windows Remote Desktop Services” / “RDP” (instant component recognition) (Rapid7)
- “privilege escalation to SYSTEM” (clear outcome; security teams triage by outcome) (Krebs on Security)
- “CISA KEV” + a concrete deadline date (operations teams search the mandate language) (NVD)
- “Patch Tuesday February 2026” (the weekly/monthly workflow hook) (Krebs on Security)
If you’re optimizing this article for SEO/GEO, those phrases belong in: title, intro, and at least one heading—because they match how defenders actually search when they’re under time pressure.
Where CVE-2026-21533 fits in the real attack chain
A local EoP in an RDP component is rarely the “first step.” It’s usually step 3 또는 4:
- Initial access (phish, token theft, exploit, malvertising, etc.)
- Land as a standard user (or low-priv service context)
- Escalate to SYSTEM fast and quietly
- Establish persistence, dump creds, pivot laterally, disable defenses
CVE-2026-21533’s value is that step (3) becomes more reliable 그리고 less noisy than improvising with misconfigurations or living-off-the-land escalation attempts that often fail on modern baselines.
The service-config angle reported publicly suggests a common post-compromise pattern: if you can change how a privileged service is configured or what it references, you can often route execution or trust to attacker-controlled inputs—then turn that into admin membership changes or token-level jumps. (컴퓨터)
A practical prioritization model
Step 1: Patch priority, based on exploit reality—not category labels
Because this is in KEV and marked exploited, you prioritize it like you would a remote code execution affecting crown-jewel servers: schedule, approve, execute. (NVD)
Step 2: Prove remediation, don’t assume it
For local EoP bugs, the usual failure mode is “we patched 일부 rings.” You want high-confidence proof:
- A device is on a patched build (or has the relevant cumulative update)
- The vulnerable component path is actually updated
- Telemetry shows no post-compromise indicators during the patch window
Because MSRC pages are JS-rendered and patch mappings vary by Windows version/channel, many teams use a combination of:
- Windows Update compliance reporting (Intune/ConfigMgr)
- Endpoint query (PowerShell/WMI/registry build numbers)
- Vulnerability scanners (Tenable/Rapid7 plugins once available)
Verification playbook: enterprise-safe checks you can run today
아래는 다음과 같습니다. defender-oriented checks. They are meant to validate posture and catch suspicious outcomes (service config tampering + admin group modifications) without providing exploit instructions.
1) Find recent local Administrators group changes
PowerShell (local machine):
# List local Administrators group members (baseline snapshot)
Get-LocalGroupMember -Group "Administrators" |
Select-Object Name, ObjectClass, PrincipalSource
Windows Security Event Log hunt (centralized):
If you have Security logs collected, look for events associated with local group membership changes. In many environments:
- 4728/4729 (member added/removed from a security-enabled global group)
- 4732/4733 (member added/removed from a security-enabled local group)
Exact event IDs can vary based on policy and where the change happens, so test on a known change in a lab and confirm your environment’s telemetry.
2) Watch for service configuration changes
PowerShell (services config diff):
# Snapshot key service properties for diffing over time
Get-CimInstance Win32_Service |
Select-Object Name, DisplayName, StartMode, State, PathName, ServiceType, StartName |
Sort-Object Name |
Export-Csv ".\\services_snapshot.csv" -NoTypeInformation
Run it daily on high-risk endpoints/servers and diff the CSV. You’re hunting for unexpected changes in:
PathName(binary path / arguments)StartName(service account)StartMode(Auto where it wasn’t)
3) Endpoint telemetry query: suspicious service modification behavior
If you ingest process creation (e.g., Sysmon Event ID 1 or Defender for Endpoint device process events), start with behavior patterns like:
sc.exe config/sc.exe sdset사용법reg.exe add타겟팅HKLM\\SYSTEM\\CurrentControlSet\\Services\\*- Writes to service-related registry keys followed by admin group modifications
This is intentionally broad: your goal is to catch the class of behavior even if the specific exploit changes.

Detection content: a starter Sigma you can adapt
This is a starting point, not a drop-in guarantee. Tune it to your log source (Sysmon, EDR, Windows native).
title: Suspicious Service Configuration Change Followed by Local Admin Modification
id: 7b0d7d5b-2f2b-4f6b-9f7a-0a9c6b9f2c33
status: experimental
description: Detects suspicious service configuration/registry modifications often used in post-compromise privilege escalation chains, plus local admin group changes.
author: SOC Engineering
date: 2026/02/16
references:
- <https://nvd.nist.gov/vuln/detail/CVE-2026-21533>
- <https://www.cisa.gov/known-exploited-vulnerabilities-catalog>
tags:
- attack.privilege_escalation
- attack.persistence
logsource:
product: windows
category: process_creation
detection:
selection_tools:
Image|endswith:
- '\\sc.exe'
- '\\reg.exe'
- '\\net.exe'
- '\\net1.exe'
selection_sc:
CommandLine|contains:
- ' config '
- ' sdset '
- ' failure '
selection_reg:
CommandLine|contains:
- 'HKLM\\SYSTEM\\CurrentControlSet\\Services\\'
selection_net_localgroup:
CommandLine|contains:
- ' localgroup '
- ' Administrators '
- ' /add'
condition: selection_tools and (selection_sc or selection_reg or selection_net_localgroup)
falsepositives:
- Legitimate admin / IT automation tools
- Software deployment scripts
level: medium
Why this helps for CVE-2026-21533 specifically: public reporting points at service configuration key modification plus privilege escalation outcomes like adding a local admin user. (컴퓨터)
Patch Tuesday context: related CVEs you should mention
CVE-2026-21533 didn’t land in isolation. February 2026 Patch Tuesday coverage repeatedly groups it with five other actively exploited issues. This matters operationally because attackers don’t run “one CVE.” They run a chain.
From widely cited February 2026 roundups, the exploited set includes:
| CVE | 구성 요소 | 카테고리 | Why it clusters with 21533 |
|---|---|---|---|
| CVE-2026-21533 | Windows Remote Desktop Services | 권한 상승 | Post-compromise jump to SYSTEM (Rapid7) |
| CVE-2026-21519 | 데스크톱 창 관리자 | 권한 상승 | Another SYSTEM path; complementary escalation option (Krebs on Security) |
| CVE-2026-21525 | Remote Access Connection Manager | 서비스 거부 | Disruption + defense evasion opportunities in foothold phase (Rapid7) |
| CVE-2026-21510 | Windows Shell | Security Feature Bypass | Reduces “are you sure?” friction at click time (Rapid7) |
| CVE-2026-21513 | MSHTML Framework | Security Feature Bypass | Similar “friction removal,” often paired with lure delivery (Rapid7) |
| CVE-2026-21514 | Microsoft Word | Security Feature Bypass | Document-based entry that can feed post-compromise escalations (Krebs on Security) |
If you’re building a remediation narrative for stakeholders: position 21533 as the post-compromise accelerator inside a broader month where multiple bugs either increase initial access probability (bypasses) or increase capability after access (EoP). (Rapid7)
Hardening moves that reduce repeatability
Patching closes the known hole. Hardening reduces the chance that the next bug in the same class becomes catastrophic.
- Reduce local admin sprawl If users routinely run as admins, privilege escalation bugs become less meaningful. Tighten local admin membership, adopt JIT/JEA patterns where possible.
- Audit service modification rights Many escalation chains depend on who can write service configuration or service registry keys. Regularly review permissions on sensitive services and watch for drift.
- Turn “RDP present” into “RDP governed” Even if you don’t expose RDP externally, ensure RDP-related components and policies are part of your standard baseline: logging, EDR coverage, update rings, and configuration control.
- Treat KEV as an SLO, not a headline KEV entries create a defensible operations SLA: patch by due date, prove compliance, then keep evidence for audit. (NVD)
If your team uses Penligent as an AI-assisted pentesting and validation workflow, CVE-2026-21533 is a clean use case for what most vulnerability programs struggle with:
- translating “patch now” into machine-verifiable evidence that devices are no longer exposed,
- validating that common post-compromise signals (service tampering, local admin creation) are being detected and routed,
- producing a repeatable report that security, IT, and leadership can all sign off on.
In other words: not “scan harder,” but prove the fix 그리고 prove the monitoring—especially when KEV deadlines force compressed timelines.
If you want adjacent context from Penligent’s own library on the February 2026 exploited cluster (feature bypasses and real-world patch workflow framing), the internal links at the end are the most relevant.
리소스
- NVD — CVE-2026-21533: https://nvd.nist.gov/vuln/detail/CVE-2026-21533 (NVD)
- CVE.org record — CVE-2026-21533: https://www.cve.org/CVERecord?id=CVE-2026-21533 (CVE)
- CISA alert (KEV additions, includes CVE-2026-21533): https://www.cisa.gov/news-events/alerts/2026/02/10/cisa-adds-six-known-exploited-vulnerabilities-catalog (CISA)
- CISA KEV catalog (searchable): https://www.cisa.gov/known-exploited-vulnerabilities-catalog (CISA)
- BleepingComputer — February 2026 Patch Tuesday (includes CrowdStrike quote about service config key modification): https://www.bleepingcomputer.com/news/microsoft/microsoft-february-2026-patch-tuesday-fixes-6-zero-days-58-flaws/ (컴퓨터)
- Rapid7 — Patch Tuesday February 2026 (tables + exploitation flags): https://www.rapid7.com/blog/post/em-patch-tuesday-february-2026/ (Rapid7)
- Tenable — February 2026 Patch Tuesday coverage (includes CVE-2026-21533 notes): https://www.tenable.com/blog/microsofts-february-2026-patch-tuesday-addresses-54-cves-cve-2026-21510-cve-2026-21513 (Tenable®)
- CrowdStrike — Patch Tuesday analysis (mentions active exploitation; credits/attribution context): https://www.crowdstrike.com/en-us/blog/patch-tuesday-analysis-february-2026/ (CrowdStrike)
- ZDI — February 2026 Security Update Review (structured CVE list): https://www.thezdi.com/blog/2026/2/10/the-february-2026-security-update-review (Zero Day Initiative)
- Sophos — February Patch Tuesday overview: https://www.sophos.com/en-us/blog/februarys-patch-tuesday-assumes-battle-stations (SOPHOS)
- KrebsOnSecurity — Patch Tuesday February 2026 edition: https://krebsonsecurity.com/2026/02/patch-tuesday-february-2026-edition/ (Krebs on Security)
- CVE-2026-21510 (Windows Shell bypass) — Penligent: https://www.penligent.ai/hackinglabs/cve-2026-21510-poc-the-smartscreen-moment-that-never-happens/ (펜리전트)
- CVE-2026-21509 (Office zero-day context) — Penligent: https://www.penligent.ai/hackinglabs/microsoft-patches-office-zero-day-cve-2026-21509-exploited-in-the-wild/ (펜리전트)
- CVE 2026 landscape roundup — Penligent: https://www.penligent.ai/hackinglabs/cve-2026-the-vulnerability-landscape-when-identity-breaks-and-legacy-code-bites-back/ (펜리전트)


