In today’s hyper-connected landscape, cybersecurity is no longer about perimeter firewalls or manual pentesting cycles — it’s about resilience, automation, and real-time adaptability. 사이버 범위 environments are now at the heart of this transformation.
A Cyber Range is a controlled, high-fidelity simulation environment that allows security professionals to test, validate, and improve their cyber defenses under real-world attack conditions — without risking production systems. Originally used by military and intelligence agencies, cyber ranges have evolved into powerful training and testing platforms for enterprises, SOC teams, and AI-driven security operations.
In the AI era, where threat surfaces are expanding faster than human teams can handle, the integration of automation, simulation, and adaptive learning through Cyber Ranges provides a strategic edge. It allows red, blue, and purple teams to collaborate in dynamic threat environments — continuously improving their skills and defense posture.
This article explores the architecture, applications, and AI integration of Cyber Ranges, and how next-generation intelligent testing tools like Penligent.ai are redefining the way cybersecurity teams validate and strengthen their defenses.
Why Cyber Range Matters in the AI Era
Traditional cybersecurity testing once relied heavily on static methods — manual pentests, rule-based vulnerability scans, and fixed incident response playbooks. These approaches fail to scale against today’s polymorphic, automated threats. Cyber Ranges fill this gap by offering dynamic, continuous, and repeatable simulation ecosystems.
- Bridging the Skills Gap With the shortage of skilled cybersecurity professionals, Cyber Ranges act as virtual bootcamps. They enable realistic, repeatable training under live-fire conditions — from basic phishing simulations to advanced zero-day exploits.
- Enhancing Team Collaboration In a Cyber Range, red teams (attackers), blue teams (defenders), and purple teams (hybrid coordinators) operate in one unified space. AI-based systems can dynamically adjust attack intensity, forcing defenders to adapt and evolve, creating a continuous feedback loop between offense and defense.
- Adaptive Threat Emulation Modern ranges incorporate AI threat models that evolve as adversaries do. Instead of replaying the same attack patterns, AI-driven simulators mutate tactics, techniques, and procedures (TTPs) to mirror current APT behavior — turning training into a living, breathing war game.
- Resilience through Realism By mimicking enterprise network topology, IoT endpoints, and industrial control systems (ICS/SCADA), Cyber Ranges replicate the complexity of real infrastructures. This realism ensures that security measures validated in the range actually hold in production.
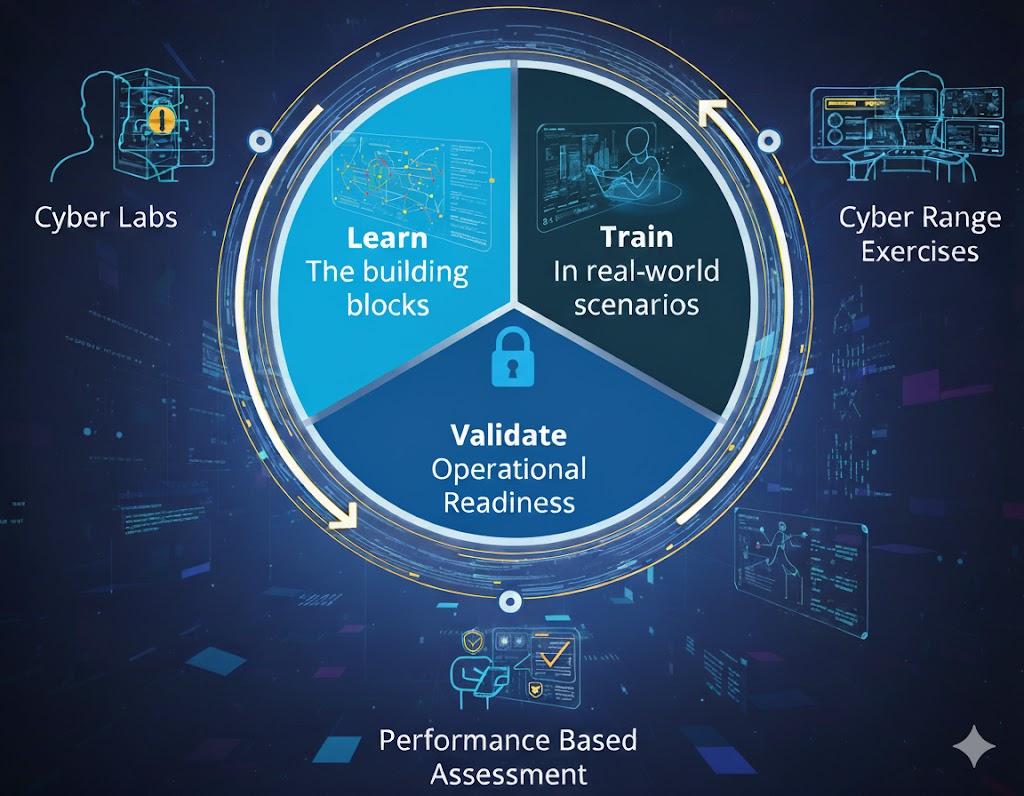
Core Architecture & Technical Components of a Cyber Range
A well-designed Cyber Range mirrors the structure and behavior of a real enterprise network — but in a fully isolated, controllable environment. Its architecture typically consists of several integrated layers that work together to deliver realism, scalability, and measurable training impact.
| Layer | 설명 | Key Technologies |
|---|---|---|
| Infrastructure Layer | Virtualized servers, routers, IoT, and ICS assets forming the attack surface | VMware, KVM, Docker, Kubernetes |
| Network Emulation Layer | Simulates live traffic, routing, latency, and bandwidth constraints | GNS3, Mininet, ns-3 |
| Scenario Orchestration Layer | Defines attack/defense sequences and scenario progression | Ansible, Terraform, Python APIs |
| Threat Simulation Layer | Generates realistic offensive operations, including exploits and malware | Metasploit, Cobalt Strike, Atomic Red Team |
| AI/Analytics Layer | Uses ML to adjust difficulty and measure participant performance | TensorFlow, PyTorch, Elastic Stack |
To illustrate how orchestration works, consider the following YAML configuration that defines a simple simulated network with two hosts and one attacker:
# cyber_range_scenario.yaml
scenario:
name: "AI-enhanced Red Team Drill"
topology:
nodes:
- name: web-server
type: vm
os: ubuntu
role: target
- name: db-server
type: vm
os: ubuntu
role: target
- name: attacker
type: container
image: kali:latest
role: red_team
network:
links:
- from: attacker
to: web-server
- from: web-server
to: db-server
automation:
scripts:
- path: /opt/attack_scripts/sql_injection.py
- path: /opt/attack_scripts/privilege_escalation.sh
This configuration creates a self-contained testbed where AI algorithms can dynamically alter the attack scripts’ behavior based on defense response data — providing infinite training permutations
Use Cases & Real-World Scenarios
Cyber Ranges are used across industries and government sectors for multiple operational and training goals. Below are the five most impactful use cases:
- Enterprise Defense Training Simulate phishing, insider threats, ransomware propagation, or DDoS attacks to evaluate detection and incident response readiness.
- Red-Blue-Purple Team Collaboration Establish a continuous training cycle where offensive and defensive units operate under realistic constraints, building stronger communication and adaptive strategies.
- Zero-Day Exploit Validation Before patch deployment, test zero-day exploits within the range to assess risk exposure safely.
- Compliance & Certification Testing Validate network configurations and data flows against NIST, ISO 27001, or GDPR standards in a safe, repeatable way.
- Academic and Workforce Development Universities and training centers deploy Cyber Ranges as experiential learning platforms for the next generation of cybersecurity professionals.
Example:
Below is a Python snippet to automate a simulated phishing campaign for red-team testing:
from faker import Faker
from smtplib import SMTP
fake = Faker()
target_users = ["[email protected]", "[email protected]"]
def send_phish(user):
message = f"Subject: Security Alert\\n\\nDear {user.split('@')[0]},\\nYour account will expire soon. Click here to renew."
with SMTP('smtp.fakecompany.local') as smtp:
smtp.sendmail("[email protected]", user, message)
for u in target_users:
send_phish(u)
This script mimics phishing attack traffic while logging response metrics, enabling defenders to measure detection accuracy.
Automation & AI Integration in Cyber Ranges
The integration of AI 그리고 automation has transformed Cyber Ranges from static, rule-based sandboxes into dynamic, adaptive learning ecosystems. Within these environments, AI-driven orchestration systems can autonomously:
- Generate and mutate attack paths based on MITRE ATT&CK frameworks
- Adjust difficulty dynamically according to defender responses
- Score and evaluate blue-team decisions using reinforcement learning models
Example pseudocode demonstrating AI-driven attack automation:
from ai_threat_simulator import AIAttackPlanner
planner = AIAttackPlanner(model="mitre_gpt")
attack_plan = planner.generate_plan(target="corp_network", difficulty="adaptive")
planner.execute(attack_plan)
This system continuously evolves as defenders respond — dynamically modifying tactics, payloads, and timing — creating a realistic, adversarial training loop that mirrors live attack pressure.
Integration Highlight: Penligent.ai — AI Attack Engine Targeting Cyber Ranges
While Cyber Ranges serve as the defensive battleground, Penligent.ai acts as the AI-powered adversary—a next-generation offensive testing platform designed to continuously challenge, exploit, and validate Cyber Range defenses.
Within this offensive–defensive ecosystem, Penligent.ai can:
- Launch autonomous, multi-vector penetration tests against Cyber Range environments (cloud, IoT, hybrid infrastructures)
- Adapt attack behavior using AI-driven reinforcement models that learn from each defensive reaction
- Exploit vulnerabilities discovered during simulation, then automatically document and score system resilience
- Feed back intelligence to improve the next attack iteration, building a closed-loop adversarial learning cycle
| Aspect | Cyber Range (Defensive Side) | Penligent.ai (Offensive Side) |
|---|---|---|
| 목적 | Defense training and resilience validation | Automated AI-driven attack and validation |
| Function | Simulates enterprise infrastructure | Executes adaptive penetration testing |
| Feedback Loop | Collects defensive metrics | Generates attack intelligence and evolution |
| 결과 | Team readiness and response benchmarking | Continuous threat adaptation and exploit discovery |
By turning the Cyber Range into a live-fire target environment, Penligent.ai brings authenticity and unpredictability to the training process. Instead of scripted exercises, defenders face real adaptive adversaries — continuously probing, exploiting, and evolving.
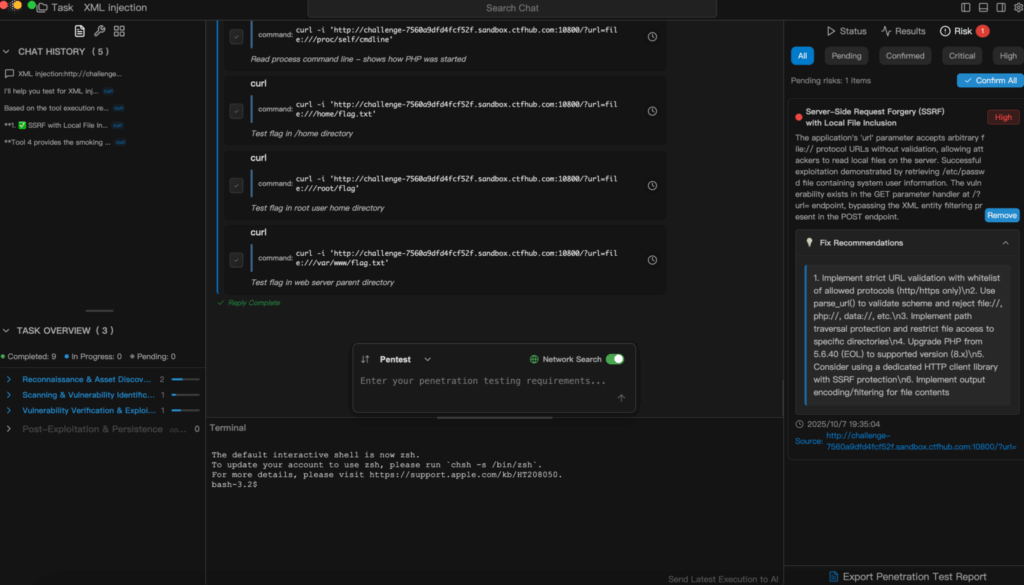
This integration marks a paradigm shift: Cyber Ranges are no longer isolated testbeds—they become living ecosystems where AI attackers and human defenders evolve together, pushing the boundaries of modern cybersecurity readiness.
Cyber Range in Enterprise Security Operations
For enterprises, Cyber Ranges play multiple operational roles:
| Objective | Implementation | Benefit |
|---|---|---|
| Training & Skills Validation | Simulated attacks for SOC teams | Boosts incident response speed |
| Tool Validation | Test EDR, SIEM, IDS performance | Identifies false positives and gaps |
| Policy & Workflow Testing | Run response drills under controlled chaos | Improves coordination between teams |
| AI Model Training | Feed simulated attack data into ML pipelines | Enhances predictive defense systems |
Conclusion: The Cyber Range as the Future of Proactive Defense
The Cyber Range is no longer a niche educational experiment — it’s the strategic nerve center of modern cybersecurity. As threats grow more automated and adversarial behavior becomes increasingly AI-driven, security teams cannot afford to rely on passive defenses or static audits. Instead, continuous, AI-assisted simulation and validation — as pioneered by platforms like Penligent.ai — will define the next generation of cyber resilience.


