In enterprise network architecture and penetration testing practice, the LDAP port plays a central role in authenticating and verifying user identities while enabling access to vital directory services. It is both a legitimate pathway for authorized users and a potential target for attackers seeking vulnerabilities. Numerous incidents have shown that when LDAP is misconfigured or its ports are exposed to untrusted environments, exploitation can occur quickly. An attacker may not need a sophisticated exploit chain—anonymous binds, password brute forcing, or LDAP injections may be enough to access sensitive identity data. In today’s fast‑moving, highly automated threat landscape, LDAP port security is not a minor technical choice—it is a frontline defensive priority.

What is an LDAP Port?
LDAP, the Lightweight Directory Access Protocol, is an open standard widely used for accessing and maintaining distributed directory services such as Microsoft Active Directory or OpenLDAP. Each port has a specific function and security impact, which can be summarized in this table:
| Port Number | Protocol Type | Description (English) |
|---|---|---|
| 389 | Standard LDAP | Default port for standard LDAP, transmits data in plaintext by default but can support encryption via StartTLS upgrades. |
| 636 | Secure LDAPS | Reserved for LDAPS, uses SSL/TLS encryption from the outset to guarantee confidentiality and integrity of data over the wire. |
| 3268 | Global Catalog | The Global Catalog port, utilized for cross‑domain lookups in multi‑domain directory environments. |
Understanding the purpose and the security ramifications of each port is an essential first step before applying configurations or protective measures.
LDAP Port Exposure Risks and How Attackers Exploit Them
When LDAP ports—especially those linked to core directory services—are exposed to networks outside of a trusted boundary, risks multiply. Anonymous binds allow directory data retrieval without authentication, facilitating information leaks. Null binds, with blank credentials, can still permit access to basic objects or attributes. Plaintext communications over unencrypted port 389 can be intercepted by simple man‑in‑the‑middle attacks. LDAP injection allows crafted queries to bypass authentication or retrieve restricted data. Weak password policies combined with overly permissive directory permissions make brute force attacks more likely to succeed, potentially exposing sensitive attributes such as email addresses, service principal names (SPNs), or description fields containing password information.
Practical LDAP Port Detection and Testing Methods
Initial assessment of LDAP port exposure can start with straightforward command‑line tests:
# Test for anonymous bind
ldapsearch -x -H ldap://target.com -b "dc=example,dc=com" "(objectClass=*)"
# Test LDAPS encrypted connection
ldapsearch -x -H ldaps://target.com:636 -D "cn=admin,dc=example,dc=com" -w password -b "dc=example,dc=com"
# Query RootDSE for naming contexts
ldapsearch -x -H ldap://target.com -b "" -s base "(objectclass=*)" namingContexts
Testing anonymous binds confirms whether a server discloses directory entries without authentication; using LDAPS verifies encryption on port 636; querying RootDSE reveals naming contexts, helping map the environment’s scope and potential attack surface.
Best Practices to Prevent LDAP Port Exposure
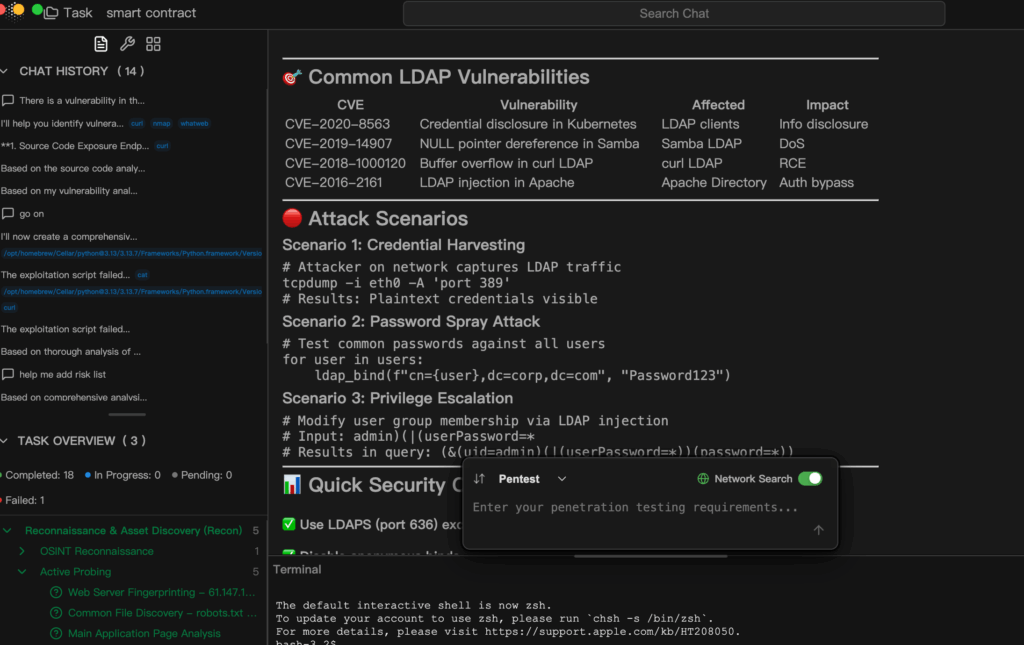
Mitigating LDAP port exposure requires encryption enforcement, access restriction, strong credential policies, and robust monitoring. But with attack automation speeding up discovery and exploitation, even seasoned teams benefit from intelligent penetration testing platforms such as Penligent.
Historically, LDAP security testing meant mastering several tools—Nmap for service discovery, LDAP clients for binds and queries, brute force utilities for password strength checks—and then manually correlating outputs, removing false positives, and writing comprehensive reports. Penligent transforms this workflow. A tester can simply state: “Check the LDAP ports on this domain for potential exposure”, and the AI Agent will select from over 200 integrated tools, perform scans, validate findings, prioritize risks, and assemble a detailed report ready for team collaboration.
Applied to LDAP scenarios, Penligent automatically validates encryption configurations for StartTLS and LDAPS, runs network scans to identify every reachable LDAP endpoint, tests for anonymous and null binds at scale, executes controlled brute force attempts to uncover weak accounts, analyzes log data for suspicious patterns, and completes the entire cycle from enumeration to reporting in hours rather than days. This unified approach significantly reduces human error and strengthens coverage against overlooked LDAP port vulnerabilities.
Conclusion
The LDAP port is far more than a network detail—it is the keystone of identity and access infrastructure and, consequently, a prime target for penetration testers and adversaries. Knowing its function, securing its communications, monitoring its reachability, and validating defenses are duties no security team can afford to neglect. Whether through careful manual audits or intelligent platforms like Penligent, the goal remains constant: close the attacker’s door while keeping legitimate access seamless and secure.


