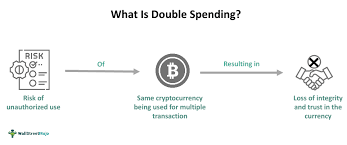
AI finds TOCTOU double-spend risk
Time-of-Check–Time-of-Use race conditions are a class of timing bugs that bridge the space between a system’s decision point and the moment that decision is acted upon. In blockchain payment flows, such a gap can be the difference between a single valid purchase and a double-spend. When code reads a balance, then later applies a purchase, an attacker who can submit almost-simultaneous transactions or exploit reordering can make the check succeed twice while the state update only occurs once. That’s the heart of the double-spend TOCTOU.
How Penligent works
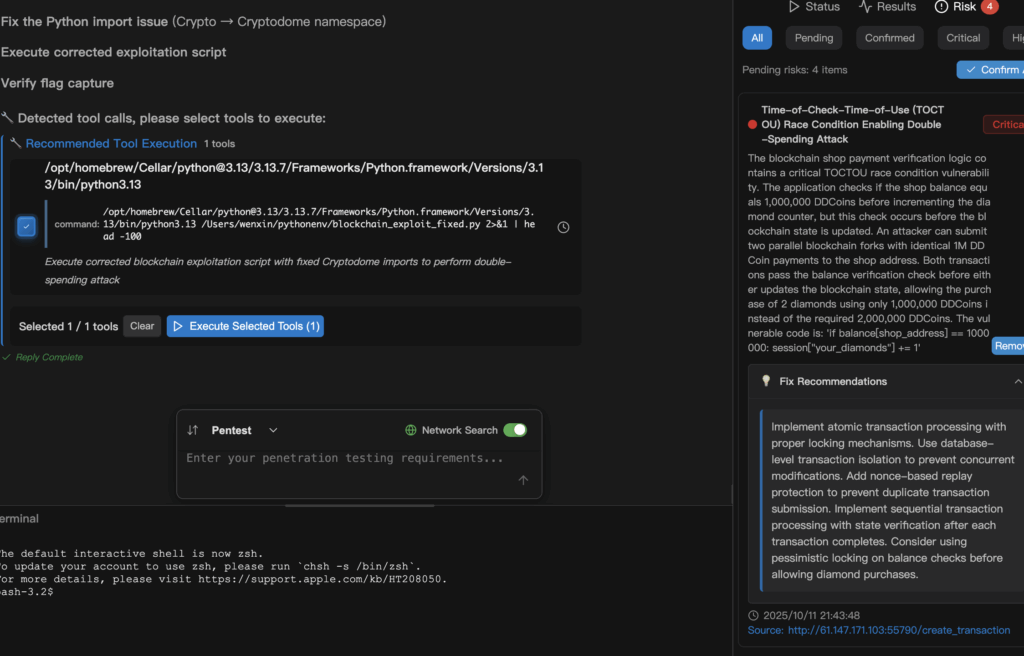
Penligent’s approach to finding these issues is not guesswork. It starts with static analysis patterns that flag “check-then-act” idioms — lines of code where balance or entitlement is read and a subsequent write updates an entitlement counter. These flagged locations receive context: the code path’s call graph, the network endpoint that invokes it, and the environmental assumptions it makes (e.g., “assumes single-threaded updates” or “assumes block confirmations before next step”). With this context, Penligent triggers controlled verification: non-destructive probes against staging endpoints, correlation with transaction traces when available, and targeted concurrency tests that sample behavior under near-simultaneous submissions.
Concretely, a vulnerable flow might look like this in production: the application checks balance[shop_address] == 1_000_000 and then increments the buyer’s diamond count. An attacker submits two 1,000,000 DDCoin transactions that arrive within the window between the check and the effective state change. Because the check runs before either transaction is committed, both checks pass, and the user gains two diamonds while only spending one unit of the asset. Penligent assembles evidence by collecting the request/response traces, transaction IDs, block timestamps, and any observable race artifacts, then binds them to the static code location that performs the check.
How to Fix TOCOTOU
Fixing TOCTOU in blockchain contexts usually means making the balance check and state change atomic. On traditional backends, that means database transactions with strong isolation levels and mutexes or optimistic concurrency schemes with retries. On smart contracts, that means designing the contract so state transitions are executed in a single transaction, or using mechanisms like nonces and explicit per-account sequence numbers to prevent replayed or duplicated operations. The following safe pseudocode shows the defensive pattern, emphasizing atomicity and correctness rather than attackability:
# defensive pseudocode: atomic update inside a serializable transaction
with db.transaction(isolation="serializable"):
if balance[shop_address] >= PRICE:
balance[shop_address] -= PRICE
session["your_diamonds"] += 1
else:
raise InsufficientBalanceError()
Operationally, additional measures help: require nonces or monotonic counters in transaction submissions, maintain strict ordering of operations at the API gateway, and instrument full traceability so that concurrent submission patterns can be reconstructed. Rate limiting and batching can also reduce the practical window in which concurrency can be exploited.
From the detection perspective, Penligent’s real value lies in fusing signals. Static indicators alone generate many false positives; runtime telemetry alone lacks direct connection to source code. Penligent ties static code findings to real execution evidence: which endpoints were called, which transaction IDs were observed on-chain, and which sequence of events led to a state divergence. The result is an evidence bundle that’s actionable: developers receive the exact source lines to fix, operations get the transaction traces to validate a reversal or mitigation, and security teams gain a prioritized remediation plan.
For teams adopting this model, the workflow becomes faster and more accountable. Instead of months of manual triage, you get reproducible evidence and a clear remediation path. The fix is as much about engineering as it is about process: product owners must accept atomicity constraints, operations must ensure transactional isolation in deployment, and security must validate mitigations with targeted re-runs.
Suggested Penligent prompt (natural language) — for internal use
If you want Penligent to scan for TOCTOU-style double-spend risks on a given service, a concise prompt could be:
“Scan the payments endpoint at https://staging.example.com/create_transaction for TOCTOU and double-spend race conditions. Focus on code paths that read balances or entitlements then write state. Generate non-destructive verification samples, correlate any concurrent transaction traces, and produce an evidence bundle with source locations and prioritized fixes.”
This prompt instructs Penligent to combine static pattern matching with safe runtime validation and evidence correlation.


