O que é uma ferramenta de adulteração?
Uma ferramenta de adulteração é qualquer utilitário, biblioteca, driver, script ou binário que um adversário (ou um testador) usa para modificar, interromper ou ocultar a operação do software, da telemetria ou do estado do sistema - geralmente para desativar a detecção, alterar evidências, aumentar privilégios ou persistir.
A "ferramenta de adulteração" abrange muitos aspectos:
- Tamperadores de EDR/AVScripts/binários que interrompem ou neutralizam agentes de endpoint.
- Drivers no modo kernel usado para manipulação privilegiada (incluindo BYOVD - Traga seu próprio motorista vulnerável).
- Manipuladores de processo e memória (Process Hacker, procexp, LiveKD, Frida, gdb).
- Violadores de registros/arquivos que excluem/sobrescrevem rastros.
- Adulteradores de protocolo/pacote que alteram as comunicações (mitmproxy, ferramentas baseadas em scapy).
- Cadeias de ferramentas de adulteração física ou de firmware (JTAG, flashes, kits de solda).
Essa definição é intencionalmente ampla: as ferramentas de adulteração são definidas pelo efeito e não pela forma - seu trabalho é alterar o que o defensor pensa que é o estado do sistema.

Por que as ferramentas de adulteração são importantes agora
Os atacantes preferem o caminho de menor resistência. Derrubar o defensor (adulteração) é frequentemente mais barato do que contorná-lo. Tendências observadas:
- Terminação EDR/AV é comum no início das intrusões; os adversários orquestram a eliminação de processos, cargas de drivers e adulteração de ganchos para impedir a detecção antes do movimento lateral.
- BYOVDNo entanto, o que acontece é que os invasores carregam drivers de terceiros assinados, mas vulneráveis, para obter privilégios do kernel e encerrar as proteções do espaço do kernel.
- Famílias de ferramentas de adulteração (adulteradores de registros como o "Spawnsloth", scripts assassinos de EDRs, patchers de memória) aparecem em campanhas do mundo real e são frequentemente reutilizados em intrusões.
Três implicações operacionais:
- A adulteração é geralmente a primeira etapa ativa da linha do tempo do ataque. Detecte-o com antecedência e você interromperá a cadeia de ataque.
- As ferramentas de adulteração podem ser muito pequenas e utilizar binários que não estão na terra (LOLbins). Observe o comportamento e a ancestralidade do processo, não apenas os nomes dos arquivos.
- A detecção deve incluir visibilidade em nível de kernel e proteção de telemetria. Apenas as assinaturas não são suficientes.
Tipos e casos de uso comuns de ferramentas de adulteração
| Categoria | Exemplos de ferramentas | Finalidade / Estágio de ataque |
|---|---|---|
| Tamperadores de processo no modo de usuário | ProcessHacker, procexp, pskill, scripts personalizados do PowerShell | Eliminar/modificar processos de EDR, desativar serviços |
| Drivers no modo kernel | Drivers vulneráveis assinados (BYOVD), LiveKd, rootkits do kernel | Obter persistência e controle a partir do espaço do kernel |
| Violadores de memória/tempo de execução | Frida, gdb, injetores personalizados | Funções de gancho, verificações de tempo de execução de patches, ocultação de cargas úteis |
| Violadores de registros/arquivos | Scripts personalizados, módulos do tipo "Spawnsloth | Apagar ou modificar evidências (registros, registros de eventos do Windows) |
| Assinatura de código/violação de impressões digitais | Ferramentas de reempacotamento, uso indevido do signatário | Reassinar binários maliciosos ou evitar verificações de integridade |
| Violadores de rede/mitm | mitmproxy, kits de ferramentas scapy | Interceptar e modificar a API/tráfego de comando e controle |
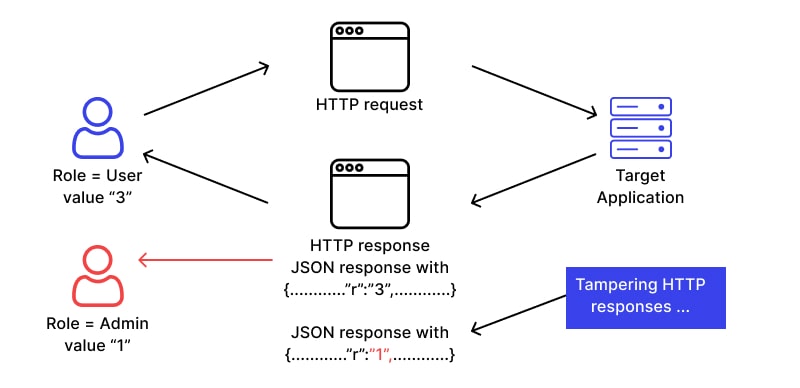
Exemplo de fluxo de campanha em que aparecem ferramentas de adulteração
- Acesso inicial (phish/exploração)
- Aumento de privilégios (exploração local, BYOVD)
- Violação: desative o EDR, elimine os agentes de monitoramento, limpe os registros
- Movimento lateral e coleta de credenciais (Mimikatz ou derivados)
- Persistência e exfiltração de dados
Observe as análises publicadas: vários relatórios de fornecedores e de informações sobre ameaças mostram que a violação ocorre consistentemente nas etapas 2 a 3.
Padrões de detecção: sinais que você deve instrumento
A) Anomalias no ciclo de vida do processo
- Criações de processo inesperadas com relações pai-filho suspeitas (por exemplo,
svchost -> powershell -> processhacker) - Processos auxiliares de curta duração usados para eliminar serviços
- Utilitários de aparência legítima sendo executados a partir de caminhos incomuns
B) Anomalias de controle de serviço e SCM
- Repetido
Gerenciador de controle de serviçoschamadas de parada/terminação seguidas de tentativas de reinicialização (possível loop de DoS de recuperação de término) - Serviços temporariamente renomeados ou removidos para impedir a reinicialização (observado em ataques direcionados)
C) Eventos de carga/descarga do driver
- Novo carregamento de driver no modo kernel de fornecedores não padrão ou com assinaturas incomuns
- Hashes de driver ou nomes de driver vulneráveis conhecidos (detecção BYOVD)
D) Registro e adulteração de integridade
- Lacunas nos registros de data e hora do fluxo de eventos/syslog
- Exclusão inesperada ou truncamento de registros (comportamento semelhante ao spawnsloth)
E) Lacunas de telemetria / pontos cegos do agente
- Baixa telemetria de endpoints que estavam relatando anteriormente
- Correlação entre queda de telemetria e eventos de processos suspeitos
Detecções de concreto - trechos de Splunk, Sigma e Sysmon
Abaixo estão os trechos de detecção utilizáveis que você pode inserir em seu SIEM (adapte os nomes dos campos ao seu ambiente).
Splunk: detectar a parada do agente de ponto de extremidade seguida pelo carregamento do driver
index=wineventlog EventCode=7040 OR EventCode=7045
| eval svc=coalesce(ServiceName, ProcessName)
| search svc="YourEDRServiceName" OR svc="MsMpSvc"
| stats count by _time, ComputerName, svc, EventCode, Message
| sort - _time
| where EventCode=7040 OR EventCode=7045
Regra Sigma (processo spawn -> procexp)
Título: Possível execução de ferramenta de adulteração - ProcessHacker/ProcExp
id: 4f9d1b7b-xxxx
status: experimental
Descrição: Detecta a execução suspeita de ferramentas frequentemente usadas para adulterar o EDR.
origem dos registros:
produto: windows
detecção:
selection:
Image|endswith:
- '\\ProcessHacker.exe'
- '\\\procexp.exe'
- '\\\vmmap.exe'
condição: seleção
nível: alto
Evento Sysmon (config) para detectar cargas suspeitas de drivers
C:\\Windows\\System32\\drivers\\
Esses são os pontos de partida - ajuste a atividade normal do administrador: muitos desses utilitários são usados legitimamente, portanto, o contexto de alerta é fundamental.
Lista de verificação priorizada de detecção de ferramentas de violação
| Tarefa de detecção | Prioridade | Justificativa |
|---|---|---|
| Monitore a ancestralidade do processo e crie alertas para padrões incomuns entre pai e filho | Alta | Os invasores abusam dos LOLbins e de ferramentas legítimas |
| Alerta sobre eventos de parada/desabilitação do serviço EDR/AV correlacionados com logins locais | Alta | Sinal direto de tentativas de adulteração |
| Registrar e alertar sobre cargas de motoristas de fornecedores não incluídos na lista branca | Alta | BYOVD e vetor de adulteração do kernel |
| Vigilância FIM/Hash em executáveis de agentes de segurança | Médio | Detectar binários adulterados ou executáveis renomeados |
| Detecção de desvio de carimbo de data/hora e lacuna de registro | Alta | A adulteração de registros reduz o valor forense |
| Verificar os batimentos cardíacos da telemetria do agente em comparação com a integridade do processo do agente | Alta | A queda da telemetria pode indicar adulteração |
Proteção e mitigação: o que os engenheiros realmente fazem
Endurecimento defensivo
- Proteção contra violação: Proteção contra adulteração fornecida pelo fornecedor que impede a parada/desabilitação do serviço por administradores de baixo privilégio e restringe contextos não confiáveis do instalador. Observação: eficaz somente com o modelo de permissões correto.
- Fortalecimento do kernel e verificação do driver: Lista branca de drivers permitidos usando assinatura de código e listas de permissão de fornecedores; bloquear drivers vulneráveis conhecidos.
- Canais de telemetria imutáveis: Os agentes de endpoint devem tentar canais seguros alternativos para enviar a telemetria se o caminho principal da telemetria sofrer interferência; verifique também a integridade da fonte no lado do servidor.
- Lógica de recuperação de serviços: Proteger a reinicialização automática do serviço com reconciliação de estado para que o agente reconstrua seu estado de detecção após a reinicialização (não apenas o processo).
- Fortaleça a auditoria e o registro: Envie rapidamente os registros para fora do host (syslog/SIEM centralizado) e monitore as anomalias de transporte ou ingestão.
Política e processo
- Privilégio mínimo para administradores - remover direitos de administrador local desnecessários.
- Atualizações de agentes assinadas e imutáveis - exigem verificação criptográfica na atualização e na inicialização.
- Livros de jogo de incidentes para adulteração - ter etapas predefinidas para isolar, criar nova imagem e preservar cópias forenses se for detectada uma adulteração.
- Exercícios de adulteração da equipe vermelha - detecção de testes com casos de uso de ferramentas de adulteração autorizadas (incluindo simulações de BYOVD).
Operacionalização da detecção de adulteração com automação e IA
Vamos passar das assinaturas de detecção para a resposta e a simulação automatizadas. É nesse ponto que as plataformas de automação/controle habilitadas para IA podem acelerar a maturidade.
Simulação e validação contínua
- Simulação automatizada de violaçãoAtaques programados que tentam ações comuns de adulteração (parada de serviço, injeção de processo, carregamento de driver vulnerável) em um ambiente controlado para validar a detecção e a resposta.
- Teste de caos da resiliência do endpointManipulações de processos benignos: acione aleatoriamente manipulações de processos benignos e garanta que o pipeline de detecção os revele com a gravidade esperada.
- Testes de integridade de telemetriaValidação: valida que os agentes produzem batimentos cardíacos assinados e que o SIEM aceita/rejeita telemetria forjada.
Aumento da IA
- Linha de base comportamental: Os modelos de ML detectam desvios na telemetria multidimensional (árvores de processo, fluxos de rede, eventos de driver) mais rapidamente do que as regras estáticas.
- Priorização: A triagem de IA reduz o ruído ao correlacionar indicadores de violação com sinais de alta fidelidade da intenção do invasor (roubo de credenciais, movimento lateral).
- Execução automatizada de manuaisSe a violação for confirmada, aplique automaticamente o isolamento, colete dados forenses e bloqueie drivers ou hashes suspeitos.
Receitas de código e detecção
Abaixo estão artefatos reais: trechos de código de detecção, regras YARA e uma regra Splunk que você pode inserir e iterar.
YARA: detecta cadeias binárias comuns de adulteração
regra TamperingToolCandidates {
meta:
author = "sec-engineer"
description = "Detecta binários contendo strings típicas de ferramentas de adulteração"
strings:
$proc_hack = "ProcessHacker" nocase
$procexp = "Process Explorer" nocase
$vmmap = "VMMap" nocase
condição:
qualquer um deles
}
PowerShell: verifique se há serviços marcados como "Parados" que são executados normalmente
$critical = @("YourEDRServiceName", "YourAVService")
foreach ($svc in $critical) {
$s = Get-Service -Name $svc -ErrorAction SilentlyContinue
if ($s -and $s.Status -ne 'Running') {
Write-Output "$svc não está sendo executado em $env:COMPUTERNAME"
# escalate: enviar alerta ou tentar reiniciar com script de recuperação
}
}
Splunk: detectar a carga do driver e, em seguida, o padrão de truncamento de eventos
index=sysmon EventID=6 OR index=wineventlog EventCode=1102
| stats count by ComputerName, EventID
| where EventID=6 OR EventID=1102
| join ComputerName [ search index=wineventlog EventCode=7045 | fields ComputerName, Message ]
| where count>1
Assinaturas de detecção e suas ações de resposta
| Assinatura | Evidências | Resposta imediata |
|---|---|---|
| O serviço EDR foi interrompido na sessão de login | Evento ServiceStop + login interativo | Quarentena de host, coleta de memória, instantâneo de disco |
| Driver do kernel carregado de um fabricante desconhecido | DriverLoad EventID + incompatibilidade de assinatura | Bloqueio do carregamento do driver na política do kernel, escalonamento para IR |
| Truncamento rápido de registros | Eventos de limpeza do registro de segurança | Encaminhe uma cópia segura dos registros, isole e inicie a análise forense |
| Execução de um caminho de ferramenta de adulteração conhecido | Processo Criar eventos com caminho | Encerrar o processo, impedir a reinicialização, coletar o despejo do processo |
Penligent: como uma plataforma de pentest inteligente se encaixa
Penligente pode ser usado para simular o comportamento de ferramentas de adulteração em grandes frotas sem scripts humanos no circuito. Em vez de escrever scripts personalizados para cada combinação EDR/driver, a Penligent automatiza a matriz de ataque: ela cria cenários que tentam parar os agentes, emular cargas de driver BYOVD (em sandboxes de teste) e testar a detecção de perda de telemetria. Como modela as táticas pós-intrusão, a Penligent ajuda as equipes a validar se seus manuais de triagem são acionados corretamente quando ocorrem tentativas de violação.
Estudos de casos reais e conclusões
- Observações sobre o EDR Kill-Chain - Vários blogs de fornecedores e registros de incidentes destacam que os adversários tentam rotineiramente interromper os agentes de detecção antecipadamente. Na natureza, os invasores interrompem processos de forma graciosa, exploram bugs do produto para encerrar de forma graciosa ou usam drivers no nível do kernel para realizar o encerramento silencioso.
- BYOVD é um vetor ativo - O carregamento de drivers assinados legitimamente com vulnerabilidades conhecidas continua sendo uma técnica de alto impacto. As equipes de defesa devem manter listas de permissão de drivers e alertar sobre carregamentos anômalos de drivers.
- A adulteração de registros é um multiplicador furtivo - Desativar ou modificar os registros (por exemplo, módulos do tipo spawnsloth) reduz diretamente a visibilidade pós-incidente. O registro de log centralizado e imutável reduz esse risco.
- Operacionalizar testes de violação - Programe uma simulação contínua de adulteração; meça a latência de detecção e os falsos positivos em todos os ambientes; insira os resultados nos backlogs de engenharia.
Lista de verificação rápida para um exercício de caça à violação de 1 dia
- Inventário: lista todos os agentes de segurança de endpoint, serviços e drivers associados.
- Linha de base: registre a ascendência normal do processo para operações administrativas e ferramentas de operador conhecidas.
- Inject: execute simulações de adulteração benignas (interrompa um serviço não crítico, carregue um driver de teste permitido).
- Detectar: verificar os alertas do SIEM/EDR e escalonar os sinais ausentes.
- Correção: adicionar regras de detecção e lógica de lista de permissão de driver para lacunas observadas.
- Faça um novo teste por meio da Penligent ou da automação da equipe vermelha.
Limitações práticas e modos de falha
- Os falsos positivos são reaisO que é uma detecção de segurança: muitas operações de administração usam as mesmas ferramentas que os agentes ofensivos usam. Invista em uma detecção rica em contexto (quem executou a ação, de onde, e se foi precedida por um login suspeito).
- Os agentes podem ser atacados em várias camadasO que é necessário: uma única atenuação (por exemplo, sinalizador de proteção contra violação) não é suficiente. São necessários controles em camadas.
- A visibilidade do kernel é difícil em escalaMonitoramento e verificação completos do motorista podem ser ruidosos; agregue a telemetria para melhorar a relação sinal-ruído.


