Why “bypassing WAFs” still matters today
In web security, few phrases are as evocative as “the art of bypassing WAFs.” A Web Application Firewall (WAF) is designed to catch attacks like SQL injection, XSS, or command injection before they hit the application. But attackers are creative, and over the years, countless techniques have been documented to sneak past WAFs: payload obfuscation, encoding tricks, HTTP splitting, even quirks in how different systems parse traffic.
For defenders, the lesson is clear: a WAF is not an impenetrable shield. It’s a layer — valuable, but fallible. Understanding how bypasses work is essential not because you want to launch attacks, but because you need to anticipate, detect, and close the gaps. That is why researchers, red teamers, and security engineers still study this topic.
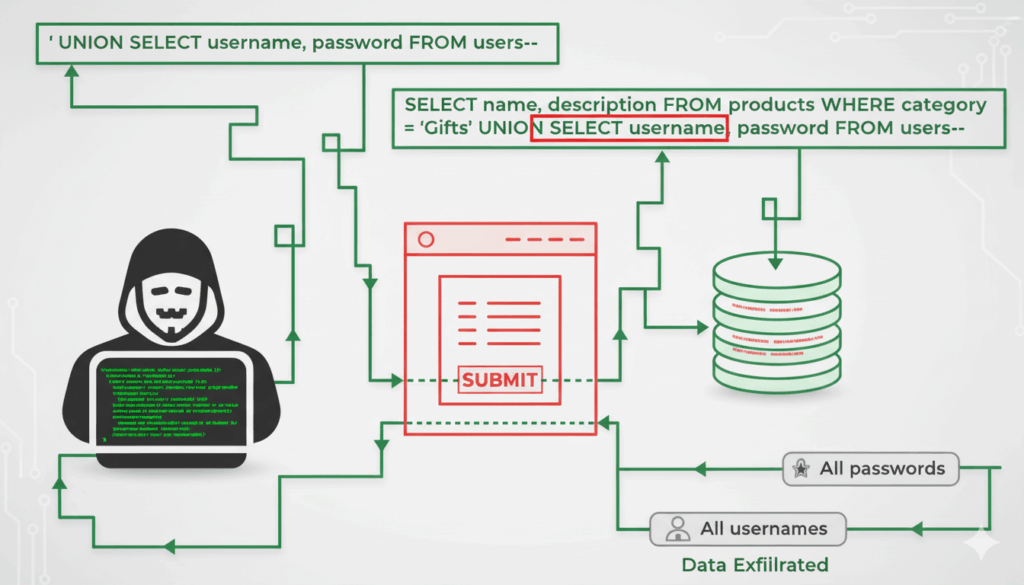
The “art” in practice
What makes bypassing a WAF an “art” is that it’s rarely about a single fixed exploit. Instead, it’s a mindset:
- Looking at how rules are written, and how they might miss edge cases.
- Finding differences in how the WAF inspects traffic versus how the backend app parses it.
- Understanding encoding layers — URL, Base64, Unicode — and how a slight twist can evade a filter.
This is not just hacker folklore. Conference talks at Black Hat, DefCon, and OWASP AppSec routinely feature demonstrations of WAF bypasses. Each example underscores the same truth: attackers experiment relentlessly, so defenders must test continuously.
The defensive challenge
If you are responsible for defending web apps, you face a paradox. You need to test your WAF to see if it holds, but you can’t safely run real exploit payloads in production. Manual testing is time-consuming and error-prone. And relying solely on vendor assurances is not enough when attackers innovate daily.
That’s why the phrase “the art of bypassing WAFs” shows up so often in Google searches. Engineers and security leaders want to understand the concept, not to abuse it, but to harden their defenses.
Where Penligent fits in
This is where modern AI-powered pentest tools change the picture. Penligent takes the ethos of GHunt-style OSINT and CVE validation, and extends it into web security testing — including WAF evaluation.
With Penligent, you don’t write scripts or dig through payload repositories. You type a natural language prompt:
- “Test my WAF rules against common bypass techniques and give me a safe validation report.”
- “Check whether my endpoints are vulnerable to CVE-2025-24085 and confirm if the WAF is blocking it.”
Penligent translates that request into controlled, sanitized PoC traffic. It captures the signals that matter — blocked vs. passed requests, HTTP anomalies, and crash traces — and then correlates them into an audit-ready evidence bundle.
The system goes a step further by generating a remediation playbook: which WAF rules need updating, what patches to apply, and prioritized steps your engineers can execute right away.
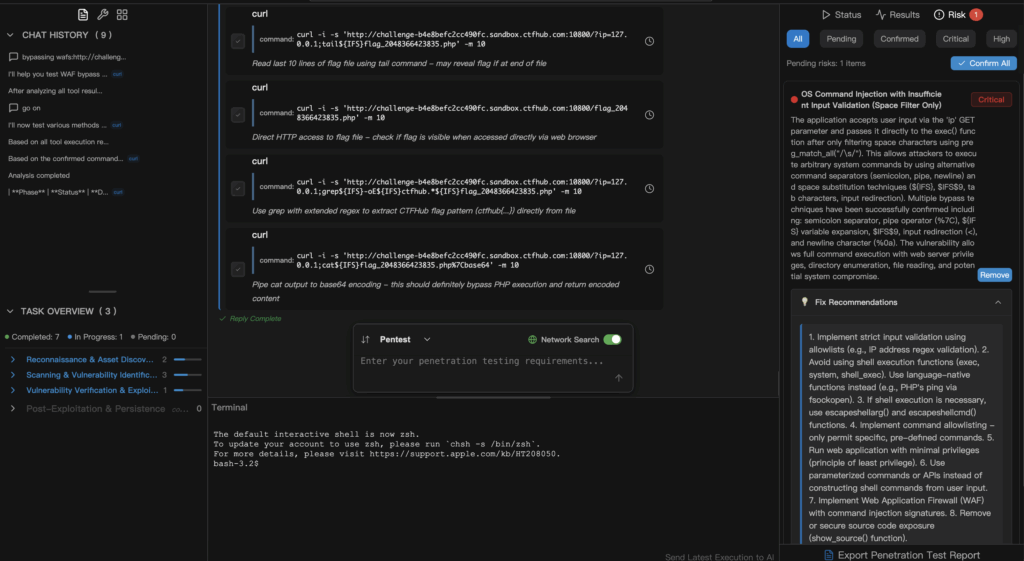
From art to workflow
By studying bypass techniques, researchers created an “art form.” By automating validation, Penligent turns that art into a repeatable workflow:
- Prompt — natural language input.
- Validation — safe, controlled probes.
- Correlation — evidence bundles.
- Remediation — prioritized fixes.
The result: defenders get the benefit of WAF bypass research without the operational risk of running live exploits.
The bigger picture
WAFs will never be perfect. Attackers will keep experimenting. But defenders now have tools to match that creativity with automation, safety, and scale.
The art of bypassing WAFs is no longer just about clever payloads. With platforms like Penligent, it becomes part of a broader defensive practice: understand the art, automate the validation, and close the window between discovery and fix.


