OAST anlamı kuruluşlar geleneksel tespitten kaçan güvenlik açıklarına uyum sağladıkça modern siber güvenlik konuşmalarında giderek daha fazla atıfta bulunulmaktadır. Bu makalede şu konulara odaklanıyoruz OAST anlamı modern uygulama güvenliğinde temel bir kavram olarak-Bant Dışı Uygulama Güvenlik Testi-ve alaka düzeyini, nasıl çalıştığını, yaygın araçları, tehdit kullanım durumlarını, savunma uygulamalarını ve doğrudan çalıştırabileceğiniz veya uyarlayabileceğiniz örnek saldırı ve hafifletme kodunu açıklar. Bu ayrıntı düzeyi aşağıdakiler için özel olarak hazırlanmıştır sert yapay zeka ve güvenlik mühendisleri karmaşık sistemler inşa etmek veya savunmak.
Güvenlikte OAST Ne Anlama Geliyor?
OAST (Bant Dışı Uygulama Güvenlik Testi) meydana gelen etkileşimleri gözlemleyerek güvenlik açıklarını belirleyen bir test metodolojisidir bir uygulamanın normal istek/yanıt döngüsünün dışında. Geleneksel Dinamik Uygulama Güvenlik Testi (DAST), doğrudan test uzmanına döndürülen yanıtlara dayanır, ancak birçok güvenlik açığı -örneğin Kör SQL enjeksiyonu, Kör SSRF veya Kör XSS-normal yanıtlarda görünür değildir. OAST, aşağıdaki durumları tetikleyen bir yük enjekte ederek çalışır test eden tarafından kontrol edilen harici bir sunucuya geri aramaBu da bant dışı etkileşim ortaya çıktığında güvenlik açığının varlığını teyit eder. Oast+1
gibi güvenlik tarama araçlarında ZAP ve Burp SuiteOAST, kör güvenlik açığı tespitini önemli ölçüde geliştiren temel bir özellik haline gelmiştir. Edgescan+1
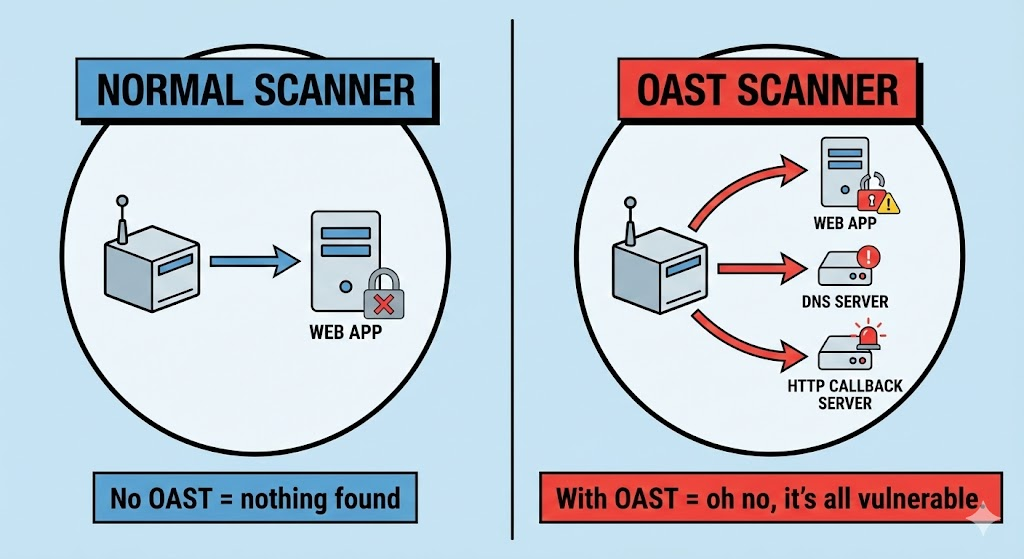
OAST Nasıl Çalışır? Mekanikler ve Protokoller
OAST testi tipik olarak bu bileşenleri içerir:
- Benzersiz Etkileşim Etki Alanı/Alt Etki Alanı - Genellikle Interactsh gibi bir OAST hizmetinden alınan, bu test döngüsüyle benzersiz bir şekilde ilişkilendirilmiş bir çözümleyici etki alanı.
- Yük Enjeksiyonu - Bu benzersiz etki alanını içeren kötü amaçlı veya test yükü.
- İzleme Sunucusu - Harici sistem gelen her türlü etkileşimi günlüğe kaydeder (DNS sorgusu, HTTP isteği, SMTP olayı, vb.).
- Onaylama Mantığı - Bir geri arama veya işaret, uygulamanın yükü işlediğini kanıtlar. HAHWUL
OAST Testinde Yaygın Reaksiyon Kanalları
| Kanal | Nasıl Çalışır | Neden Önemli? |
|---|---|---|
| DNS | Hedef uygulama OAST sunucusuna bir DNS sorgusu gönderir | Kısıtlı giden ortamlarda bile çalışır |
| HTTP(S) | Hedef, OAST etki alanına bir web isteği yapar | Daha derin etkileşimi onaylar |
| SMTP / LDAP / SMB / Diğerleri | Daha zengin etkileşim verileri için çeşitli protokoller | Çeşitli güvenlik açığı sınıflarını tespit eder |
Bu, OAST'ın geleneksel tarayıcıların yalnızca normal protokol yolunu inceledikleri için gözlemleyemedikleri gizli kusurları ortaya çıkarmasını sağlar. Edgescan
Modern Güvenlikte OAST Neden Kritiktir?
Test uzmanları, OAST ile DAST'ı birleştirerek, görünür uygulama yanıtları üretmeyen ancak dış etkileşim kanallarında gözlemlenebilir yan etkiler üretir.
PortSwigger, OAST'ın şu yollarla tanıtıldığında devrim niteliğinde olduğunu vurguluyor Burp İşbirlikçiBurp'ün Blind SQLi veya Blind OS komut enjeksiyonu gibi yeni kör güvenlik açığı sınıflarını tespit etmesini sağlar. PortSwigger
2025'te güvenlik araştırmacıları, Google Cloud üzerinde özel bir OAST altyapısı çalıştıran sofistike bir tehdit aktörünü de tespit etti. Büyük ölçekli kampanyalarda 200'den fazla farklı CVEOAST tekniklerinin kitlesel otomasyonla güvenlik açığı istismarı bir araya geldiğinde nasıl kötüye kullanılabileceğini göstermektedir. IoT OT Güvenlik Haberleri

OAST'yi Destekleyen Araçlar ve Platformlar
Birçok modern güvenlik aracı entegre OAST desteğine sahiptir:
- ZAP OAST Desteği: DNS/HTTP(S) etkileşimleri için yerleşik dinleyiciler ve BOAST, Interactsh vb. ile entegrasyon. ZAP+1
- Burp Suite İş Ortağı: Kör koşulları tespit etmek için OAST geri çağrıları sağlar. PortSwigger
- Interactsh: Birçok protokolü (DNS, HTTP, SMTP, LDAP, SMB, FTP) destekleyen OAST etkileşimleri için güçlü bir açık platform. HAHWUL
- BAST: OAST etkileşim olaylarını toplamak ve raporlamak için tasarlanmış bir sunucu. ZAP
Bu platformlar, güvenlik mühendislerinin geri aramaları yakalamasına ve yalnızca bant içi kanıtlara güvenmeden güvenlik açıklarını doğrulamasına yardımcı olur.
Pratik OAST Senaryoları ve Tehdit Modelleri
OAST özellikle aşağıdakilerin belirlenmesinde yararlıdır kör güvenlik açıklarıBir saldırganın sunucu üzerinde bir eylemi tetikleyebildiği ve tek kanıtın sunucunun harici bir hizmete ulaşması olduğu durumlarda.
Örnekler şunları içerir:
- Kör SSRF - Sunucu saldırgana veri döndürmez ancak giden HTTP/DNS istekleri yapar.
- Kör Komut Enjeksiyonu - Sunucu, çıktı göstermek yerine giden trafiği tetikleyen kodu çalıştırır.
- Kör XSS - Kalıcı kod, kurban bağlamlarında yürütüldüğünde geri arama davranışını tetikler. Edgescan
Kurumsal bir savunucu, bilinen bir OAST etki alanına giden trafiği gösteren bir AlphaSOC uyarısı görebilir, bu da potansiyel yetkisiz istismar veya yanlış yapılandırmayı gösterir. AlphaSOC
Örnek Kod: OAST Simülasyonu ve Tespiti
Aşağıdakiler 5 doğrudan saldırı/savunma kodu örneği mühendislerin referans alabileceği.
Örnek 1: OAST DNS Tetikleyicisi Oluşturma (Saldırı)
bash
1TP5Bu yük OAST sunucusuna bir DNS sorgusu tetikleyecektircurl <http://example.com?callback=uniqueid.oast.pro>
Hedef bu URL'yi işlerse ve aşağıdakiler için bir DNS araması yaparsa uniqueid.oast.proOAST sunucusu sorguyu günlüğe kaydedecektir.
Örnek 2: Python ile OAST Geri Çağrısını İzleme
python
from flask import Flask, istek
app = Flask(**name**)
@app.route("/callback", methods=["GET"])
def callback():
print("OAST Etkileşimi:", request.remote_addr, request.args)
return "", 200
app.run(host="0.0.0.0", port=8080)
Bu basit sunucuyu dağıtın ve harici bir OAST dinleyicisi olarak hareket etmesi için etki alanını bir DNS girişiyle kaydedin.
Örnek 3: OAST Trafiğini Günlüğe Kaydetme ve Uyarma
python
içe aktarma günlüğü
def log_oast_event(event):
logging.basicConfig(level=logging.INFO)
logging.info(f "OAST callback from {event['ip']} with data {event['data']}")
Geri arama uyarılarını SIEM işlem hatlarına entegre etmek için bu modeli kullanın.
Örnek 4: Giden Trafiği Filtreleme (Savunma)
bash
#Güvenlik duvarı düzeyinde yaygın OAST alanlarını engelleyiniptables -A OUTPUT -d oast.fun -j DROP iptables -A OUTPUT -d oast.pro -j DROP iptables -A OUTPUT -d oast.site -j DROP
Bu, dahili sunuculardan gelen yetkisiz OAST geri çağrılarının azaltılmasına yardımcı olur.
Örnek 5: Güvenilmeyen Etkileşim Kalıplarını Reddetme
python
# Basitleştirilmiş talep denetçisi
def is_untrusted_interaction(request):
if "oast" in request.host:
True döndür
return False
Şüpheli geri arama uç noktalarını işaretlemek ve engellemek için bu işlevi WAF mantığına entegre edin.
Kodun Ötesinde Savunma Stratejisi
Kod düzeyinde kontroller gerekli olsa da, güvenlik mühendisleri bütünsel savunmaları benimsemelidir:
- Giden Trafik Kontrolü - allow-list kuralları ile giden bağlantılar için varsayılan reddetme ilkelerini uygulayın.
- Bilinen OAST Etki Alanlarını Engelle çevre güvenlik duvarlarında.
- DNS ve HTTP trafiğini izleyin OAST yüklerine benzeyen olağandışı geri arama alanları için.
- OAST'yi Test İş Akışlarına Entegre Edin (DAST + OAST taraması) proaktif olarak kör güvenlik açıklarını bulmak için.
Geniş giden engelleme, uygulamalar yanlışlıkla güvenli olmayan girdileri işlediğinde kör istismar yöntemlerinin etkisini azaltır. HAHWUL
OAST vs Geleneksel DAST/SAST
| Test Yöntemi | Kör Kusurları Tespit Eder | Harici Sunucu Gerektirir | Tipik Kullanım Örneği |
|---|---|---|---|
| SAST | Hayır | Hayır | Kod örüntüsü analizi |
| DAST | Sınırlı | Hayır | Yanıt tabanlı tarama |
| OAST | Evet | Evet | Geri arama/yan etki tabanlı testler |
OAST, yalnızca HTTP yanıt döngüsünün dışındaki yan etkiler yoluyla ortaya çıkan sorunları ortaya çıkararak dinamik testleri geliştirir.
OAST Tarzı Teknikleri Kullanan Gerçek Dünya Kampanyaları
Yakın zamanda yapılan bir araştırma Google Cloud üzerinde barındırılan özel OAST altyapısı tehdit aktörleri tarafından hedef almak için kullanılır 200 CVE değiştirilmiş tarama araçları ve OAST geri çağrıları ile. Bu durum, saldırganların kör güvenlik açıklarından giderek daha fazla yararlandığını ve savunucuların bu tür kalıpları tespit etme ihtiyacını ortaya koymaktadır. IoT OT Güvenlik Haberleri
Bu aynı zamanda savunucuların şunları yapması gerekebileceği anlamına gelir meşru güvenlik testi trafiğini kötü niyetli geri arama modellerinden ayırt etmeözellikle saldırganlar bulut sağlayıcı IP'lerini taklit ettiğinde.
Yapay Zeka Odaklı Güvenlik Testini Entegre Etme - Penligent
Modern mühendislik ekipleri için, geleneksel otomatik tarayıcılar ince kör güvenlik açıklarını gözden kaçırabilir. Gibi platformlar Penligent değer katın:
- Üretim Yapay zeka destekli OAST görev yükleri uyarlanabilir desenlerle
- Kör etkileşimlerin meydana gelebileceği uygulama yüzeylerinin haritalanması
- Gerçek riskleri önceliklendirmek için protokoller arasında geri arama kanıtlarının ilişkilendirilmesi
- Erken tespit için OAST testlerini CI/CD işlem hatlarına entegre etme
Penligent'in yapay zeka yetenekleri, statik kuralların kolayca yakalayamadığı kör güvenlik açıklarının "zayıf sinyallerini" ortaya çıkarmaya yardımcı olarak genel uygulama güvenliğini artırır.
Sonuç
Anlamak OAST anlamı-Bant Dışı Uygulama Güvenlik Testi, güvenli uygulamalar geliştiren mühendisler için çok önemlidir. Güvenlik ekipleri, DAST ve SAST ile birlikte OAST yöntemlerinden yararlanarak, geleneksel yanıt tabanlı taramada görünmeyen kör, eşzamansız güvenlik açıklarını bulabilir. Mühendisler uygun araçlar, kodlama uygulamaları ve ağ kontrolleri ile OAST geri çağrılarına dayanan istismar tekniklerini hem tespit edebilir hem de bunlara karşı savunma yapabilir ve gelişen tehditler karşısında uygulama dayanıklılığını güçlendirebilir.


