2025 yılında yapay zeka, en ileri araştırmalardan sağlıktan finansa kadar çeşitli sektörlerin temel unsurlarından biri haline geldi. büyük dil modelleri ve dolandırıcılık tespit sistemlerinden tahmine dayalı analitik motorlarına kadar. Bu entegrasyon, verimlilik ve kabiliyette çarpıcı gelişmeler sağlamış, ancak aynı zamanda geniş ve karmaşık yeni bir saldırı yüzeyi yaratmıştır. Ağlardaki, sunuculardaki ve diğer sistemlerdeki güvenlik açıklarını ortaya çıkarmak için tasarlanan geleneksel sızma testleri web uygulamalarımodel zehirlenmesi, hızlı enjeksiyon veya sinir ağlarının düşmanca manipülasyonu gibi YZ'ye özgü riskleri tam olarak ele alamaz. YZ Sızma Testi, yalnızca BT altyapısındaki değil, YZ modellerinin kendi içindeki güvenlik açıklarını keşfetmek, istismar etmek ve azaltmak için YZ odaklı yöntemler kullanarak bu boşluğu doldurur. YZ'yi hızla benimseyen ABD kuruluşları için bu tür bir güvenlik doğrulaması isteğe bağlı olmaktan çıkıp vazgeçilmez hale gelmiştir.

Yapay Zeka Nedir Sızma Testi ve Geleneksel Yöntemlerden Farkı
YZ Sızma Testi, YZ sistemlerindeki (verileri, algoritmaları ve entegrasyon mantığı) zayıflıkları belirlemeye odaklanan özel bir siber güvenlik dalıdır. Geleneksel sistemler için Otomatik Sızma Testi Araçları ağ bağlantı noktalarını, API'leri ve yazılım güvenlik açıklarını hedeflerken, YZ sızma testi kapsamı makine öğrenimi işlem hatlarına, eğitim veri kümelerine ve çıkarım zamanı davranışına kadar genişletir. Yöntemler arasında performansı düşüren veya çıktıları manipüle eden düşmanca girdiler, önyargı veya veri sızıntısını araştırmak ve minimum pertürbasyonların karar vermeyi nasıl etkilediğini araştırmak yer alır. Genellikle kaynak kodunun düzeltilmesiyle sonuçlanan geleneksel pentestingin aksine, yapay zeka odaklı testler eğitim verilerinin arındırılmasını, model mimarilerinin ayarlanmasını veya girdi sanitizasyonu gibi savunma mekanizmalarının eklenmesini gerektirebilir.
Modern Yapay Zeka Sızma Testi Araçlarının Sunması Gereken Temel Özellikler
Modern yapay zeka sızma testi araçları, temel bir dizi gelişmiş yeteneği paylaşır. YZ destekli keşif, hem geleneksel hem de YZ'ye özgü varlıkların haritasını çıkarır. Otomatik istismar zincirleri, istem enjeksiyonu veya model parametrelerinin manipülasyonu gibi gerçekçi saldırı senaryolarını çoğaltmak için birden fazla adımı bir araya getirir. LLM red teaming, özellikle dil modeline özgü zayıflıkları ortaya çıkaran diyalogsal YZ dağıtımları için giderek daha önemli hale gelmektedir. Sürekli test - genellikle Dinamik Uygulama Güvenlik Testi (DAST) aracılığıyla - her güncelleme, dağıtım veya yeniden eğitim döngüsünü doğrular. Sorunsuz CI/CD entegrasyonu, geliştirme iş akışlarında "shift-left" güvenliğini mümkün kılarken, döngü içinde insan seçenekleri, incelikli tehdit analizi için otomasyonu uzman muhakemesiyle birleştirir.
En İyi Yapay Zeka Sızma Testi Şirketleri için Seçim Kriterleri
2025'in en iyi şirketlerini seçerken inovasyon, YZ'ye özgü kapsam derinliği, kurumsal ve prototip ortamlar için ölçeklenebilirlik, uçtan uca otomasyon ve kullanıcı deneyimi, özellikle de raporlamanın netliği temel alındı. İnovasyon; tescilli yapay zeka motorlarını, takviyeli öğrenmeyi veya yeni düşman simülasyonlarını içerebilir. Derinlik, platformun sadece geleneksel bir tarayıcıyı yeniden tasarlamamasını, YZ'nin benzersiz risklerini gerçekten ele almasını sağlar. Ölçeklenebilirlik, tüm dağıtım yelpazesinde test yapılmasına olanak sağlarken, otomasyon manuel müdahaleye bağımlılığı azaltır. Açık, eyleme geçirilebilir raporlama, karar vericilerin bulgulara etkili bir şekilde yanıt verebilmesini sağlar.
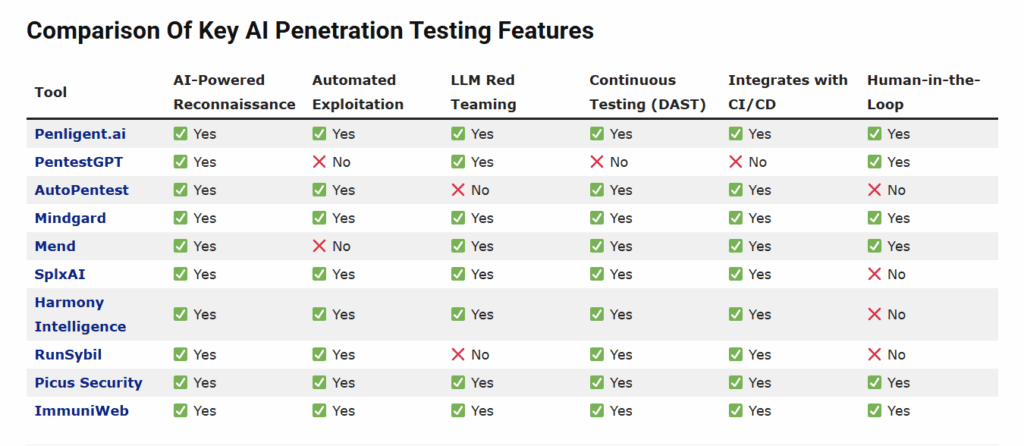
| Şirket | Güvenlik Odağı | Ana Özellikler | Avantajlar | Sınırlamalar | İçin En İyisi |
|---|---|---|---|---|---|
| Penligent.ai | Tamamen otonom yapay zeka pentest ajanı | Yapay zeka destekli keşif, otomatik istismar, LLM kırmızı ekip, sürekli DAST, CI/CD entegrasyonu, döngü içinde insan | Hacker sezgilerini taklit eder, karmaşık ağlar için ölçeklenebilir, tam yığın yapay zeka kapsamı | Daha yüksek öğrenme eğrisi, potansiyel yanlış pozitifler | Sürekli, tam otomatik doğrulama isteyen kuruluşlar |
| PentestGPT | İnsan test uzmanları için yapay zeka asistanı | Bağlama duyarlı yönlendirme, yük oluşturma, çıktı ayrıştırma; açık kaynak | Üretkenliği artırır, eğitim için idealdir, müdahaleci değildir | Otonom değil, LLM API'ye bağlı, DAST yok | Manuel iş akışlarını güçlendiren Pentesterler |
| AutoPentest | DRL tabanlı araştırma çerçevesi | DRL kullanarak otomatik keşif ve istismar; Nmap/Metasploit entegrasyonu | Akademik yenilik, özelleştirilebilir | Güçlü teknik beceriler gerektirir, ticari kullanıma hazır değildir | Araştırmacılar, akademisyenler, ileri düzey uygulayıcılar |
| Mindgard | Yapay zekaya özgü güvenlik | DAST-AI sürekli test, AI kırmızı ekip, CI/CD entegrasyonu | Yapay zekaya özgü güvenlik açıklarına odaklandı | Geleneksel ağ/uygulama pentesti yok | Modelleri güvence altına alan yapay zeka geliştirme ekipleri |
| Mend | Birleşik uygulama + yapay zeka güvenliği | Yapay zeka destekli kod taraması, diyalogsal yapay zeka testi, SBOM uyumluluğu | Geleneksel ve yapay zeka risklerini birlikte kapsar | Pure-play'e göre daha az yapay zeka uzmanlığı | Hepsi bir arada kapsama ihtiyacı duyan DevSecOps ekipleri |
| SplxAI | GenAI odaklı kırmızı ekip oluşturma | Hızlı enjeksiyon tespiti, sızıntı önleme, çok dilli destek | Gerçek zamanlı izleme, CI/CD, küresel erişim | LLM'nin ötesinde sınırlı | Küresel GenAI uygulama dağıtımları |
| Uyum İstihbaratı | Tam yığın yapay zeka odaklı saldırgan güvenlik | Otomatik tarama, gerçek zamanlı izleme, kendi kendine öğrenme | 7/24 koruma, minimum manuel çaba | İnsanlardan oluşan kırmızı ekiplerden daha az yaratıcı | KOBİ'ler ve işletmeler güvenliği otomatikleştiriyor |
| RunSybil | Hızlı yapay zeka güdümlü pentest | Hızlı kurulum, şeffaf raporlama, saldırı tekrarı | Hız + doğruluk, kullanıcı dostu | Tamamen otomatik, sınırlı özelleştirme | Startup'lar ve düzenlemeye tabi sektörler |
| Picus Güvenlik | Kontrol doğrulama + Yapay zeka içgörüleri | Sürekli BAS, Numi AI aracılığıyla öncelikli hafifletme | Etkinliği ölçer, eyleme dönüştürülebilir içgörüler | Bilinmeyenlere değil, doğrulamaya odaklanıldı | Savunmaları doğrulayan kuruluşlar |
| ImmuniWeb | Hibrit yapay zeka + insan uzmanlığı | Yapay zeka taraması, insan doğrulaması, CI/CD, sıfır yanlış pozitif SLA | Yüksek doğruluk, uyumluluğa hazır | Daha az otonom, daha yüksek maliyet | Hassasiyet gerektiren düzenlenmiş endüstriler |
Doğru Yapay Zeka Sızma Testi Ortağı Nasıl Seçilir?
Yapay zeka kullanımınıza, uyumluluk yükümlülüklerinize ve dağıtım hızınıza göre bir iş ortağı seçin. Yığınınızda diyalogsal yapay zeka hakimse, derin LLM kırmızı ekip çalışmasına öncelik verin. Kritik altyapı entegrasyonları için sürekli izleme çok önemlidir. Entegrasyon uyumluluğunu, güvenlik açığı veritabanları için güncelleme sıklığını ve satıcı destek kalitesini değerlendirin. Zaman tasarrufu ve risk azaltma avantajlarını dahil etmek için lisans maliyetlerinin ötesine bakın.
Sonuç
Yapay zeka teknolojiyi yeniden şekillendiriyor, ancak proaktif testler yapılmazsa inovasyon hızla güvenlik açığına dönüşebilir. Buradaki şirketler, farklı ihtiyaçlara uygun farklı güçlü yönler sunan AI penetrasyon testinin ön saflarını temsil ediyor. Şimdi yatırım yapmak, tehditler geliştikçe güven, uyumluluk ve esneklik sağlar.


