Even in 2025, the concept of a WPA2 password continues to serve as the fundamental barrier protecting wireless networks from unauthorized access.
For professionals engaged in network security, penetration testing, and AI-assisted vulnerability research, this passphrase is far more than a simple combination of characters; it represents the primary gatekeeper to encrypted data transmissions.
WPA2 still underpins the majority of devices currently in use, meaning it remains an essential focus for anyone committed to safeguarding network infrastructure in both home and enterprise contexts.

What is a WPA2 Password?
A WPA2 password is the security key used in the WPA2 (Wi‑Fi Protected Access 2) protocol to restrict access to wireless networks.
WPA2 builds upon and replaces earlier WPA and WEP standards, offering stronger encryption, better data protection, and more robust network access control. Its primary role is to ensure that only authorized users can connect to the Wi‑Fi network and that all data transmitted over that network remains encrypted and secure against interception.
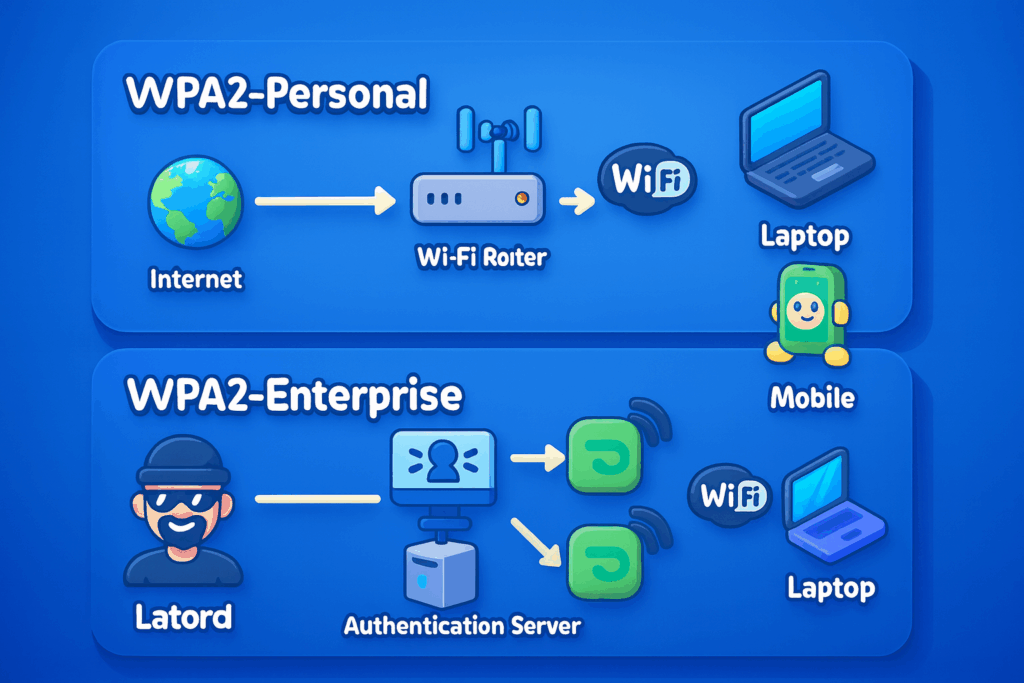
WPA2 operates in two main modes, each with different authentication methods:
- WPA2-Personal (WPA2-PSK): Common in home networks and small businesses, this mode uses a pre‑shared key (PSK) for authentication — typically a passphrase created by the network administrator during router setup. Every device joining the network must provide the same key to gain access.
- WPA2-Enterprise: Intended for larger organizations, this mode uses an authentication server — often a RADIUS server — to validate access. Instead of relying on a single shared password, each user is assigned unique credentials such as a username/password pair, digital certificates, or other identity tokens. This architecture enables per-user access control, activity logging, and tight management of large user bases, greatly enhancing overall network security.
How WPA2 Works and Why It’s Secure
The WPA2 protocol uses AES‑CCMP, combining strong encryption with integrity checks that ensure data cannot be tampered with during transmission.
Packets intercepted without the correct key are unreadable and useless to attackers. However, password strength heavily influences practical security; a weak or predictable passphrase can undermine even the most robust cryptographic defense by making the network vulnerable to brute‑force or dictionary attacks.
Example — Checking encryption type for a connected network:
# View wireless interface details
iwconfig wlan0
# Using nmcli to list encryption type
nmcli device wifi list | grep MySecureWiFi
Security researchers often perform this check prior to testing to determine whether the target is using WPA2‑PSK or WPA2‑Enterprise, and to confirm the exact encryption mode.
Penetration Testing Methodology for WPA2 Networks
During authorized penetration testing of WPA2 networks, security researchers follow a structured workflow that mirrors the strategic approach of a real‑world adversary while maintaining strict compliance with legal and ethical boundaries.
The table below presents this workflow clearly, ensuring full coverage from reconnaissance to reporting.
| Step | Description |
|---|---|
| 1. Intelligence Gathering (Reconnaissance) | Identify SSID, BSSID, operating channel, and connected clients via passive monitoring. |
| 2. Vulnerability Analysis | Check encryption type (AES‑CCMP, WPA2‑PSK) and look for TKIP fallback, outdated firmware, and misconfigurations. |
| 3. Threat Modeling | Map possible attack vectors — weak passphrase cracking, KRACK exploitation, rogue AP, MITM injection — and prioritize based on likelihood and impact. |
| 4. Password Cracking (Authorized) | Capture WPA2 handshake packets, then attempt dictionary/brute‑force attacks. |
| 5. Exploitation & Lateral Movement | Use the cracked key to access internal services and validate potential for data interception or modification. |
| 6. Reporting & Recommendations | Document all steps, tools, and findings; provide actionable improvements such as stronger passwords, disabling WPS, and upgrading to WPA3. |
This workflow remains the foundation of WPA2 penetration testing. Steps 1 and 4 are especially crucial: performing precise reconnaissance to capture the handshake, and then using authorized cracking tests to assess password strength and resilience.
Automated & AI‑Driven WPA2 Testing — with Penligent
While the structured methodology outlined above is proven and effective, it is highly manual, requiring multiple command‑line tools, careful filtering of noisy data, scripting complex tests, and manually building final reports.
Penligent radically streamlines this process by allowing a tester to issue a single natural-language instruction—such as “Analyze this WPA2 network for handshake vulnerabilities and attempt authorized password crack”—and having its AI Agent autonomously select the appropriate tools, sequence the necessary operations, verify discovered risks, and compile a detailed, prioritized report inclusive of remediation guidance.
Conclusion
The WPA2 password continues to be central in encryption protocol research and network security assessment. By combining traditional structured penetration methods with intelligent automation platforms like Penligent, researchers can conduct faster, more accurate, and more efficient testing while dedicating more of their expertise to analyzing vulnerabilities and developing effective countermeasures.


