Abstract
Cross-site scripting (XSS) remains one of the most prevalent and dangerous web vulnerabilities. Modern front-end frameworks, SPAs (single page applications), and rich third-party script ecosystems expand both opportunity and complexity. This article merges the OWASP XSS Prevention Cheat Sheet with recent academic and industry research, forming a layered defense strategy: contextual encoding, HTML sanitization, dynamic taint tracking for DOM XSS, parsing-differential fuzzing, Content Security Policy (CSP), and supply-chain controls. We further propose a design for a one-click “XSS scan” feature within Penligent, with automated pipelines, reusable scanning templates, runtime instrumentation, and report generation. This document is suitable for direct inclusion into engineering whitepapers or product documentation.
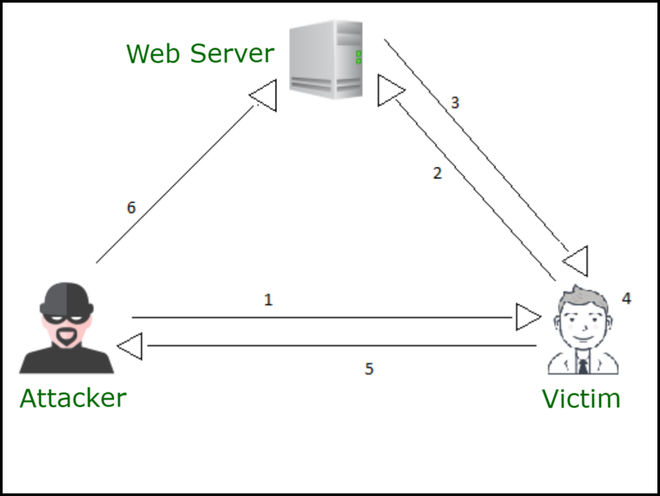
Motivation
XSS vulnerabilities enable attackers to inject executable scripts into otherwise benign web pages, effectively executing in the victim’s browser under the site’s domain privileges. These attacks can exfiltrate sensitive data (cookies, localStorage), perform unauthorized actions, or deface content. (MDN Web Docs)
Despite decades of awareness and mitigation techniques, XSS remains a persistent risk. The rise of client-side rendering, dynamic JavaScript frameworks, third-party scripts, and increasingly complex templating systems have made it harder to guarantee correctness.
Goals of this guide:
- Combine the authoritative OWASP Cheat Sheet’s practical rules with up-to-date academic and engineering research.
- Offer a robust, multi-layered defense architecture rather than a single silver bullet.
- Present a concrete design for Penligent to provide a one-click XSS scan feature, bridging research and product.
Foundations: Contextual Encoding & Safe Sinks
A core tenet of XSS prevention is: never allow raw untrusted data to reach an executable context without proper encoding or sanitization. The encoding must be appropriate to the context (HTML body, attribute, JavaScript literal, CSS, or URL). This is the essence of the OWASP XSS Prevention Cheat Sheet. (cheatsheetseries.owasp.org)
Contextual Output Encoding Rules
| Context | Unsafe Example | Safe Encoding / Mitigation |
|---|---|---|
| HTML text content | <div>${userInput}</div> | HTML entity encode (<, &, etc.) |
| HTML attribute | <img src="${url}"> | Quote attribute + attribute encoding; validate URL scheme |
| JavaScript literal | <script>var v = '${userInput}';</script> | JS string escaping (\uXXXX, escape quotes/backslashes) |
| CSS | <div style="width:${input}px"> | Strict validation, CSS escaping, or disallow dynamic CSS |
| URL / HREF | <a href="${href}">click</a> | Percent-encode, scheme whitelist (http/https), canonicalization |
In practice, always prefer built-in or well-tested encoding libraries. Avoid rolling your own ad hoc replacements.
Safe Sinks & Avoiding Dangerous APIs
Even with correct encoding, certain APIs are inherently risky. Examples of dangerous sinks include:
innerHTML,outerHTMLdocument.write,document.writelneval(),Function()constructor- Inline event handlers (e.g.
onclick="…"with dynamic content)
Prefer safe alternatives:
.textContentor.innerTextfor inserting textelement.setAttribute()(for controlled attribute names)- DOM methods (e.g.
appendChild,createElement) without string concatenation
HTML Sanitization When Rich HTML Is Needed
In scenarios where user-supplied content is allowed to include some HTML (e.g. WYSIWYG editors, comments with limited markup), sanitization is necessary. The core approach is:
- Whitelist allowed tags, attributes, and attribute value patterns.
- Use mature libraries (e.g. DOMPurify) rather than brittle custom regexes.
- Be aware of parsing-differential attacks: the sanitizer’s parsing behavior may differ from the browser’s HTML parser, leading to bypasses.
A known research line demonstrates how sanitizers and browsers can diverge in interpretation of corner-case markup, enabling escapes via alternate tokenization. (See “Parsing Differentials” research)
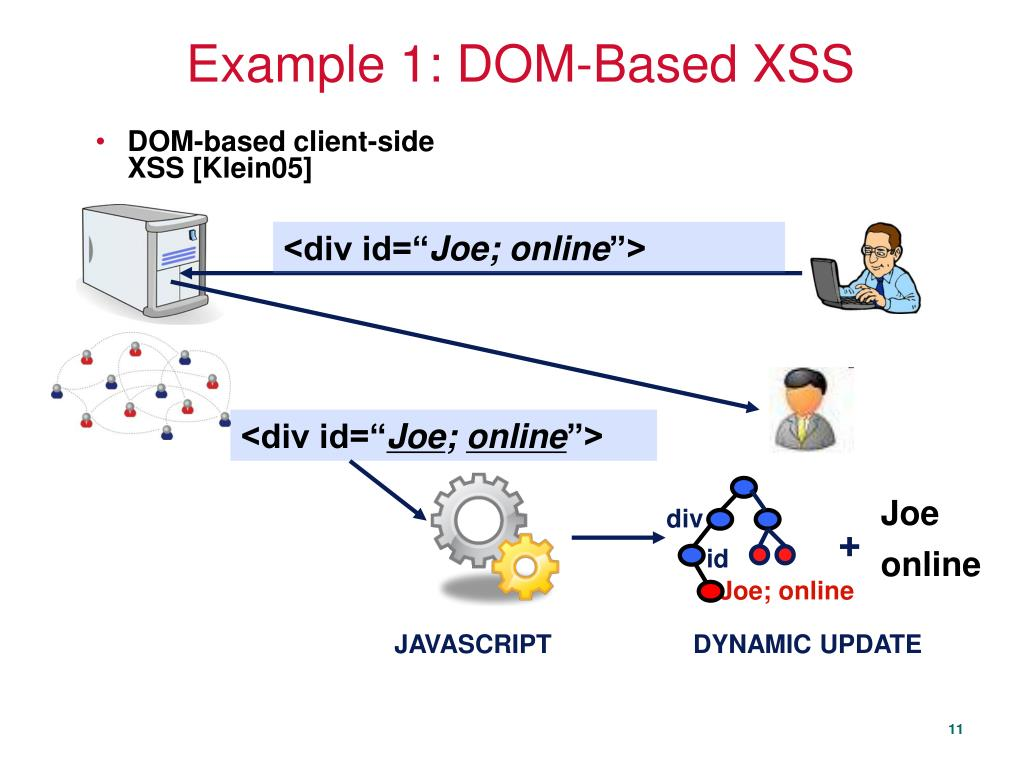
Detecting DOM-Based XSS via Runtime Taint Tracking
Server-side techniques cannot reliably catch DOM XSS (client-side injection), because the relevant sink may be in JavaScript after page load. Dynamic taint tracking (marking untrusted sources and watching propagation) is a well-studied method.
- TT-XSS (by R. Wang et al.) is a classical implementation of dynamic taint-based DOM XSS detection. (科学直通车)
- Talking About My Generation uses dynamic data flow analysis to generate targeted DOM XSS exploits. (ResearchGate)
- TrustyMon (2025) demonstrates a practical runtime monitoring system that can detect DOM-based XSS in real-world apps with high accuracy and low false positives. (ACM Digital Library)
These systems instrument client-side execution, tag untrusted inputs (e.g. URL hash, query parameters, DOM elements), and detect when they reach dangerous sinks (e.g. innerHTML) in a way that results in script execution.
One caveat: runtime tracking has performance cost. Some works combine ML/DNN as prefilter to reduce taint-tracking overhead. For example, Melicher et al. propose using deep learning to pre-classify likely vulnerable functions and apply taint tracking only there. (contrib.andrew.cmu.edu)
Example A — Fixed (use safe sink textContent)
<html>
<head><title>Welcome</title></head>
<body>
<h1>Hello!</h1>
<div id="greeting"></div>
<script>
function getQueryParam(name) {
return new URLSearchParams(window.location.search).get(name);
}
var raw = getQueryParam("name") || "";
// Use textContent to insert as plain text (safe)
document.getElementById("greeting").textContent = raw;
</script>
<p>Welcome to our site.</p>
</body>
</html>Why this is safe: textContent writes plain text; even if raw contains <script>…</script>, it will be rendered as text, not executed. Also using URLSearchParams avoids brittle index/substring parsing. portswigger.net
Example B — Attribute sink & safe URL handling (href pseudo-sink)
Vulnerable pattern:
// Vulnerable:
var params = new URLSearchParams(window.location.search);
var target = params.get("url"); // user-controlled
document.getElementById("mylink").href = target;
If target is javascript code, clicking the link executes JS.
Safe pattern (validate scheme):
function safeHref(input) {
try {
var u = new URL(input, window.location.origin);
if (u.protocol === "http:" || u.protocol === "https:") {
return u.toString();
}
} catch(e) { /* invalid URL */ }
return "#";
}
document.getElementById("mylink").href = safeHref(params.get("url"));Explanation: new URL() normalizes; we only allow http:/https: schemes. This blocks javascript:/data: schemes. portswigger.net
Content Security Policy (CSP): Defense-in-Depth
While encoding and sanitization are primary defenses, CSP provides a strong secondary barrier. A well-configured CSP using nonces or hashes, along with strict-dynamic and removal of 'unsafe-inline', can greatly restrain XSS exploitation.
However, pitfalls exist:
- Nonce reuse: Some sites reuse the same nonce across multiple responses, which undermines CSP’s protections. A recent study “The Nonce-nce of Web Security” shows that many real-world sites do this. (arXiv)
- Deployment complexity: supporting legacy inline scripts, third-party libraries, and browser inconsistencies often leads to loosening policies.
Thus, CSP should complement, not replace, encoding and sanitization.
Engineering Best Practices: CI, Lint, Testing, Monitoring
To operationalize robust XSS defenses:
- ESLint / Code linters: ban or flag usage of disallowed sinks (innerHTML, eval), require context annotations on template expressions.
- Static and dynamic analysis in CI:
- Multi-file static taint analysis for JS modules
- Fuzz testing or differential parsing tests
- Runtime instrumentation in staging environments
- Unit / security tests: generate context-based payloads in unit tests to ensure correct encoding is applied (as in “Automated Detecting & Repair of XSS Vulnerabilities” or “Detecting XSS via Unit Testing”) (arXiv)
- Monitoring and alerting: collect CSP violation reports, instrumented runtime alerts for suspicious flows, log metrics of encoding failures.
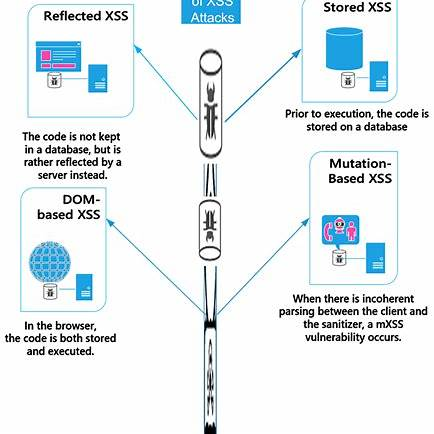
Penligent One-Click XSS Scan Design
Below is a proposed design specification you can embed into Penligent’s product as a one-click XSS scanning “Playbook”.
Task Workflow (High-level)
- Crawl & JS rendering – discover all pages and JS-driven routes.
- Static analysis – taint propagation on source code to locate high-risk sinks and functions.
- Template scanning – use templated scanners (e.g. Nuclei) to fire common XSS payloads.
- Runtime / dynamic scan – using headless browsing and instrumentation, inject payloads and detect script execution.
- Runtime taint tracking – instrument the page runtime and watch if untrusted data reaches dangerous sinks.
- Parsing-differential fuzz test – feed edge-case markup to sanitizer + browser and detect divergences.
- CSP & SRI audit – inspect headers, script tags, check for nonce reuse, missing integrity attributes.
- Report generation – assemble vulnerabilities with PoCs, risk rating, remediation suggestions, and optionally generate PR patches.
Sample Nuclei Template (Reflected XSS)
id: xss-reflect-basic
info:
name: Reflected XSS Basic
author: penligent-scan
severity: high
requests:
- method: GET
path:
- "{{BaseURL}}?q={{payload}}"
payloads:
payload:
- "<script>alert(1)</script>"
matchers:
- type: word
part: body
words:
- "<script>alert(1)</script>"You would expand with context-aware payload sets (attribute, JS, URL) and chain to headless verification to reduce false positives.
Sample Task Definition (JSON)
{
"name": "XSS QuickScan",
"steps": [
{"id": "crawl", "type": "crawler", "params": {"start_url": "{{target}}", "render_js": true}},
{"id": "static", "type": "static_analysis", "deps": ["crawl"], "params": {"analyzers": ["multi-file-taint"]}},
{"id": "template_scan", "type": "scanner", "deps": ["crawl"], "params": {"templates": ["xss-reflect-basic"]}},
{"id": "dynamic", "type": "dynamic_scan", "deps": ["template_scan", "static"], "params": {"engine": "headless-instrumented"}},
{"id": "dom_taint", "type": "runtime_taint", "deps": ["dynamic"], "params": {"agent": "instrumented-browser"}},
{"id": "parsing_diff", "type": "parsing_diff", "deps": ["dynamic"], "params": {}},
{"id": "audit_csp", "type": "csp_audit", "deps": ["crawl"], "params": {}},
{"id": "report", "type": "report_gen", "deps": ["dom_taint", "parsing_diff", "audit_csp"], "params": {"format": "pdf,html"}}
]
}Report & Output
Each finding includes:
- Type (reflected / stored / DOM)
- Proof-of-concept (HTTP request/response, DOM snapshot, screenshot)
- Severity score
- Fix suggestions (e.g. correct encoder, sanitizer config, safe API usage)
- Optionally auto-generate a patch or PR skeleton
You can also link to relevant literature (e.g. citing TrustyMon, parsing differential papers) in the internal technical report.
Sample Code Snippets & Best Practices
Here are a few illustrative safe/unsafe snippets in a React-like setting:
Unsafe (vulnerable)
function UserGreeting(props) { return ; }Safer Version
import DOMPurify from 'dompurify';
function UserGreeting(props) {
const clean = DOMPurify.sanitize(props.userContent, { ALLOWED_TAGS: ['b','i','u','a'], ALLOWED_ATTR: ['href'] });
return <div dangerouslySetInnerHTML={{ __html: clean }} />;
}Or, better:
function UserGreeting(props) {
return <div>{props.userContent}</div>; // React will auto-escape
}For attribute values:
// Unsafe
<img src={userInput} />
// Safer
function safeUrl(u) {
const doc = new URL(u, window.location.origin);
if (doc.protocol === 'http:' || doc.protocol === 'https:') {
return doc.toString();
}
return '/'; // fallback
}
<img src={safeUrl(userInput)} />Conclusion & Next Steps
This article fuses the OWASP XSS Prevention Cheat Sheet (pragmatic rules) with modern research directions (runtime taint, parsing differential, ML prefilter) to craft a robust, engineering-friendly defense approach. The one-click Penligent scan design helps productize these methods—making it easier for teams to adopt strong defenses without reinventing pipelines.


