In today’s rapidlevolving threat landscape, cybersecurity demands more than deploying protective measures. Organizations must safely and realistically simulate a variety of attack scenarios to assess how quickly and effectively teams respond under pressure. A Cyber Range functions much like a flight simulator for security professionals, offering an almost lifelike cyber battlefield where they can rehearse, validate, and refine defensive strategies without risking live systems. When enhanced by artificial intelligence, the Cyber Range transforms into a dynamic environment where learning, testing, and adapting happen faster and more accurately.

What Is a Cyber Range?
A Cyber Range is far more than a single test machine—it’s a fully functional environment that can be virtualized or deployed in a hybrid model. It replicates an organization’s IT infrastructure, including servers, databases, applications, workstations, networking devices, and simulated user activities, often with controlled internet gateways for realistic but safe training. Unlike single-point testing setups, a Cyber Range can orchestrate complex attack chains and simulate the entire breach lifecycle—from initial compromise to data theft, system disruption, and long-term persistence—allowing both defenders and attackers to practice with precision and realism.
# Example snippet from a Cyber Range network definitionnetworks:
internal:
cidr: 10.0.0.0/24
dmz:
cidr: 10.0.1.0/24
hosts:
- name: web-server
image: ubuntu:20.04
services:
- apache2
- mysql
The Importance of Cyber Range
While theoretical knowledge provides the foundation for cybersecurity expertise, successful crisis response under attack relies heavily on prior hands-on rehearsal. Cyber Ranges allow teams to acquire this operational readiness in safe conditions before facing real threats. They help organizations validate defensive mechanisms, assess the adaptability of strategies across diverse scenarios, and foster collaboration among different roles, enabling coordinated, confident responses when it matters most.
Benefits of Cyber Range and Security Gains for Organizations
The true strength of a Cyber Range lies in its ability to offer repeatable, customizable training in a fully isolated environment. Teams can refine their responses without impacting live systems, rehearse identical scenarios to explore alternative strategies, and simulate varied threats—from routine vulnerability probes to sophisticated advanced persistent threats (APTs). Cyber Ranges also serve as ideal platforms for evaluating how security products perform in particular attack sequences. This combination of safety, diversity, and repeatability delivers measurable improvements in defensive capabilities without prohibitive costs.
Who Needs a Cyber Range Platform and Why
Large enterprise security teams rely on Cyber Ranges to stress-test existing defense strategies, train SOC analysts, and coordinate responses across departments during complex incidents. Penetration testing firms use them to simulate client-specific environments for delivering more relevant and actionable reports. Governments and military organizations leverage them to conduct national-scale cyber exercises, while universities and training providers incorporate them into programs to give students immersive, hands-on learning experiences far beyond textbook theory.
Comprehensive Guide to Cyber Range Exercise Types
In a Cyber Range, the type of exercise you select determines how closely your training simulates real-world cybersecurity challenges. Different exercise formats cover the entire spectrum from offense to defense and can be tailored to specific technical goals or business scenarios. Below is an in-depth breakdown of several common and highly practical types of Cyber Range exercises:
Red Team vs. Blue Team Engagements
In this format, the red team acts as the attacker, employing penetration testing, vulnerability exploitation, social engineering, and other techniques to breach the target network. Meanwhile, the blue team serves as the defender, actively monitoring, analyzing, and responding to threats. The process sharpens both teams’ ability to adjust strategies under pressure, improve attack vector analysis, and enhance defensive systems and cross-department coordination.
# Red Team engagement example
$ red-team exploit --target web-server --payload sqlmap
# Blue Team detection example
$ blue-team monitor --rule-id SQLiDetectRule
Automated Vulnerability Detection and Exploitation Simulations
These exercises focus on verifying and optimizing the operational effectiveness of automated security tools. For instance, deploying Nmap, Nuclei, OpenVAS, or AI-powered vulnerability scanners within the Cyber Range allows for comprehensive asset discovery, followed by exploitation testing using automated frameworks. This helps evaluate automated penetration capabilities and the efficiency of rapidly finding and fixing vulnerabilities.
$ nuclei -t cves/ --target <https://demoapp.corp>
$ openvas-cli --scan target:10.0.1.45 --export vuln_report.json
AI-Assisted Attack and Defense Drills
With artificial intelligence entering the picture, exercises are no longer limited to static, pre-scripted attack scenarios. AI can adapt attack pathways or defense strategies in real time based on data generated during the exercise. For example, integrating an AI penetration assistant like Penligent enables attackers to dynamically select the most effective exploitation methods, while defenders receive automated risk analysis and remediation guidance. This exercise format tests both human-machine collaboration and the reliability of intelligent systems.
Incident Response Simulations
This type focuses on rehearsing the full process of reacting to security incidents such as data breaches, ransomware outbreaks, and zero-day exploits. It covers detection, alerting, analysis, isolation, remediation, and post-incident reviews, testing the team’s decision-making speed, communication quality, and execution under pressure.
Compliance Testing and Audit Drills
Designed around standards such as PCI-DSS, ISO 27001, and SOC 2, these exercises help teams validate whether their systems, processes, and documentation comply with required benchmarks. The goal isn’t merely to pass audits, but to instill standardized security management practices into everyday operations.
Real-World Use Cases of Cyber Range Platforms
From intensive skill training for cybersecurity teams, to testing product effectiveness and refining security policies, Cyber Ranges play a key role across industries. They are critical in supporting vulnerability research projects and enabling automated penetration testing workflows in controlled conditions. At national and sectoral levels, Cyber Ranges are the preferred choice for cyber warfare drills, enabling both defenders and adversaries to prepare for real engagement.
How to Build or Choose the Right Cyber Range Solution
Selecting or building a Cyber Range requires careful consideration. Decisions should account for budget, desired scope, and integration with existing security stacks. It is important to ensure support for multiple, customizable attack scenarios, evaluate the trade-offs between cloud-based and on-premise deployment, and consider scalability in line with organizational growth. Increasingly, organizations should verify that their Cyber Range can integrate AI capabilities for advanced testing and automation.
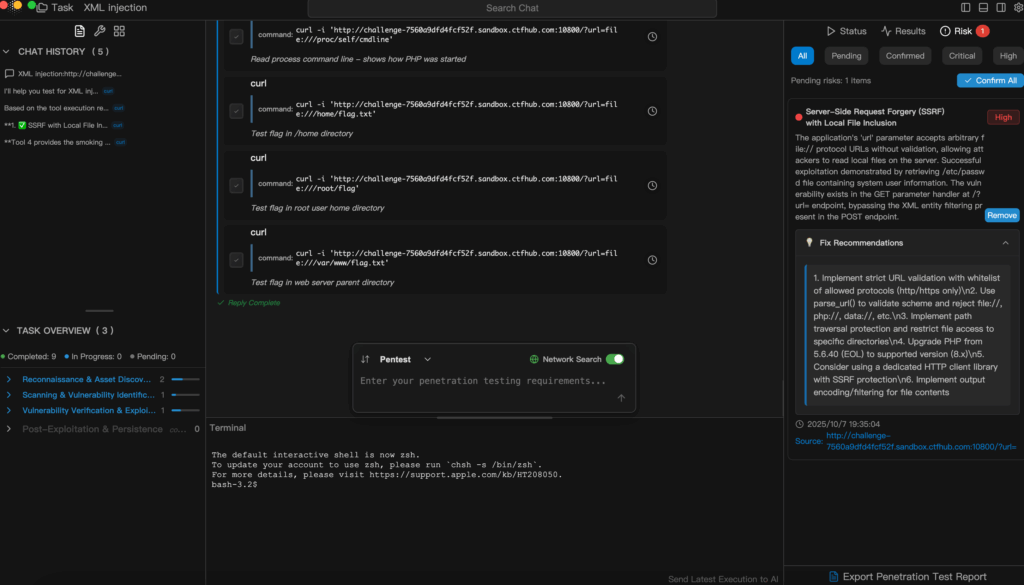
AI-Driven Cyber Range Testing: The Penligent Intelligent Penetration Case
Traditionally, Cyber Range sessions depend on manual tool selection, test execution, results analysis, and report generation—all of which consume considerable time. Artificial intelligence changes this landscape. Penligent, the world’s first Agentic AI Hacker, empowers teams to initiate penetration testing through plain language, bypassing the need for command-line input. It automates the full cycle from asset discovery to vulnerability validation by intelligently choosing from over 200 integrated security tools, running scans, filtering false positives, and producing structured reports complete with remediation recommendations. With Penligent deployed in a Cyber Range, tests are no longer limited to static simulations—they become dynamic, on-demand exercises that reflect the complex realities of modern cyber threats, and they can be completed in hours or minutes instead of days.