Para digitalização de aplicativos significa usar ferramentas automatizadas ou manuais para detectar, inventariar e analisar cada software executado em dispositivos, servidores, plataformas de nuvem e redes corporativas. Esse processo ajuda as organizações a identificarem aplicativos aprovados e não autorizados, software desatualizado ou vulnerável, implantações de TI sombra e malware oculto. Ao realizar a varredura de aplicativos regularmente, as organizações obtêm visibilidade total do ambiente de software, fortalecem a postura de segurança, mantêm a conformidade e reduzem o risco de ataques cibernéticos vinculados a aplicativos não gerenciados ou inseguros.
Em resumo: A varredura de aplicativos fornece um inventário de software completo e em tempo real e protege a sua organização contra riscos de segurança causados por aplicativos não gerenciados ou potencialmente prejudiciais.
O que significa "Scan for Application"?
Quando falamos em varredura de aplicativos, estamos falando em descobrir qual software existe em seu ecossistema (endpoints, nuvem, contêineres, dispositivos móveis), auditar se cada instância é autorizada, avaliar se cada versão é atual e segura e correlacionar as descobertas com vulnerabilidades ou ameaças ocultas. Isso às vezes é chamado de descoberta de aplicativos, digitalização de inventário de ativos de software, detecção de programas, auditoria de aplicativos de endpointou simplesmente varredura de aplicativos para conformidade de segurança. O aumento do SaaS, o uso de endpoints remotos e o BYOD tornam a visibilidade total do software inegociável nas arquiteturas de segurança modernas.

Por que a varredura de aplicativos é essencial para a segurança e a conformidade A varredura de aplicativos é importante:
Em ambientes de TI complexos, os aplicativos não gerenciados representam vários riscos: TI invisível (funcionários que desenvolvem aplicativos fora da governança), malware oculto incorporado em softwares menos conhecidos e programas desatualizados ou sem suporte que se tornam vetores de ataque. De acordo com a documentação do fornecedor de inventário de ativos, os fluxos de trabalho de verificação de inventário são essenciais para a visibilidade e a auditoria em tempo real. manageengine.com
| Benefício | Por que é importante |
| Visibilidade da segurança | Conheça todos os programas instalados para impedir ameaças desconhecidas |
| Detecção de ameaças | Identifique aplicativos de TI maliciosos, não autorizados ou obscuros |
| Conformidade | Atender às normas ISO 27001, SOC 2, HIPAA, PCI-DSS e regras de licenciamento |
| Gerenciamento de patches | Identificar aplicativos desatualizados e vulneráveis |
| Inventário de ativos | Manter registros completos dos ambientes de software |
Além disso, ferramentas empresariais recentes, como as detalhadas pela Licenseware, mostram uma convergência entre o reconhecimento alimentado por IA e a varredura de inventário de software, indicando o crescente interesse do mercado por cliques em frases como gerente de inventário de software e descoberta de aplicativos que geram alto engajamento na pesquisa. SOFTWARE DE LICENÇA
Quais fases estão incluídas em uma varredura completa do aplicativo?
Uma verificação robusta de aplicativos não é uma execução de ferramenta única - ela segue um ciclo de vida. Aqui estão os estágios - e por que cada um deles é importante.
1. Planejamento e definição do escopo - Defina seus limites
Antes de clicar em "verificar", esclareça quais dispositivos, servidores, cargas de trabalho em nuvem e pontos de extremidade do usuário estão incluídos. Defina quem tem acesso, quando a varredura será executada e como os resultados serão aproveitados. Sem isso, você corre o risco de perder ativos ou causar interrupções na produção.
2. Descoberta e enumeração - Encontre tudo
É aqui que os agentes ou varreduras de rede enumeram cada pacote de software instalado, serviço em segundo plano, extensão, imagem de contêiner ou aplicativo móvel. Ferramentas como o Configuration Manager da Microsoft permitem que você visualize os ciclos de inventário de software. Microsoft Learn A menos que você saiba o que está lá fora, você simplesmente não pode protegê-lo.
3. Detecção de vulnerabilidades e riscos - Separe a segurança do risco
Depois de ter o inventário, examine esses aplicativos em busca de versões desatualizadas, CVEs conhecidos, configurações incorretas ou sinais de presença não autorizada. É nesse ponto que a varredura de aplicativos se transforma em varredura de vulnerabilidades - mas observe: a varredura de aplicativos trata de descoberta, não exclusivamente de exploração de fraquezas.
4. Relatórios e priorização - O que corrigir primeiro?
Uma lista de softwares descobertos não é útil a menos que você saiba quais itens são mais importantes. Relatórios eficazes categorizam por gravidade, capacidade de exploração, impacto nos negócios e relevância para a conformidade. Isso ajuda a concentrar a correção no que representa o maior risco.
5. Remediação e redimensionamento - Feche o ciclo
Corrija os problemas (patch, remoção, configuração) e, em seguida, execute uma varredura de acompanhamento para verificar a resolução. A varredura contínua cria uma cadência de visibilidade e controle - sem uma nova varredura, você não pode afirmar que fechou a lacuna.
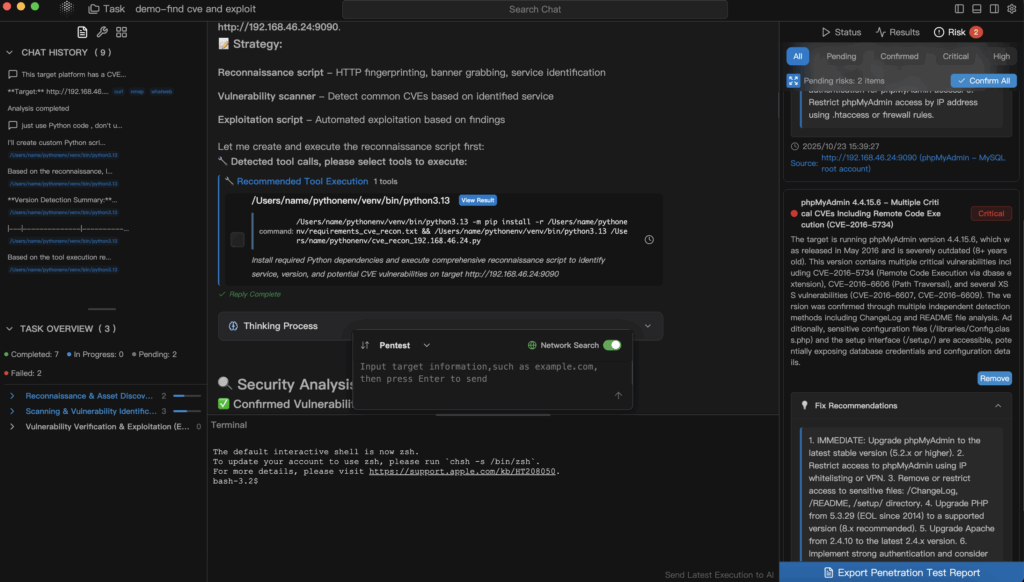
Como fazer a varredura de aplicativos
A varredura de software usa uma variedade de técnicas em vários ambientes. Considere os seguintes métodos:
- Varreduras de agentes de endpoint: Instalado em cada estação de trabalho/servidor para monitorar as alterações.
- Análise do sistema de registro/arquivo: Detecta aplicativos instalados e modificações.
- Inspeção do gerenciador de pacotes: Para Linux/macOS/contêineres (por exemplo,
apto,cerveja,npm). - Varreduras de carga de trabalho e contêineres na nuvem: Descubra aplicativos executados em cargas de trabalho efêmeras.
- Varredura baseada em dispositivos móveis/MDM: Captura de aplicativos em dispositivos gerenciados/não gerenciados.
Exemplo: Comando simples de inventário do Linux
dpkg -get-selections > software_list.txt
Exemplo: Trecho do Windows PowerShell
Get-WmiObject -Class Win32_Product | Select-Object Name,Version | Export-Csv apps_inventory.csv
| Categoria de ferramentas | Finalidade | Exemplos |
| Varredura de endpoints e sistemas operacionais | Descubra o software instalado | Microsoft Intune, Jamf |
| Scanners de vulnerabilidade | Sinalizar versões com falhas de segurança conhecidas | Tenable Nessus, Qualys |
| Gerenciamento de ativos de software (SAM) | Visibilidade de licenciamento e conformidade | Lansweeper, Licenseware |
| Descoberta de nuvem/SaaS | Encontre aplicativos de nuvem não gerenciados | Wiz, Prisma Cloud |
| Visibilidade de aplicativos aprimorada por IA | Detectar software oculto ou não autorizado | Penligente |
Plataformas modernas como Penligente simplificam todo esse fluxo de trabalho, descobrindo automaticamente aplicativos em ambientes híbridos, sinalizando softwares não autorizados ou de risco e fornecendo orientações inteligentes de correção. Com a varredura contínua e a visibilidade centralizada, as equipes podem identificar rapidamente as ameaças e agir antes que os invasores as explorem.
Onde a Penligent pode melhorar o escaneamento de aplicativos
Em organizações focadas em testes de penetração automatizados e integração de ferramentas de segurança, plataformas como a Penligent oferecem valor avançado. Ao combinar a descoberta de aplicativos, a varredura contínua, a correlação de riscos e os fluxos de trabalho de correção guiada, a Penligent permite que as equipes de segurança passem da "descoberta de software" para a "correção de riscos de forma proativa". Por exemplo, quando a varredura de inventário sinaliza um aplicativo não aprovado em um endpoint remoto, a automação da Penligent pode acionar uma avaliação de vulnerabilidade de acompanhamento ou uma ação de contenção. Isso vincula a fase de inventário de aplicativos diretamente aos fluxos de trabalho de seu centro de operações de segurança (SOC).
No mundo dos testes de penetração automatizados, a falta de um aplicativo não gerenciado ou oculto significa que um vetor de ataque não será testado. A Penligent garante que o escopo do seu teste de penetração não se limite aos ativos conhecidos, mas inclua todos os aplicativos que sua organização executa, conhecidos ou ocultos. Isso cria um ciclo de descoberta → vulnerabilidade → correção → validação, alinhando-se com as melhores práticas de higiene cibernética.
Práticas recomendadas e erros comuns
Práticas recomendadas Automatize as programações de varredura (diária ou semanalmente), use credenciais privilegiadas para obter visibilidade total, inclua endpoints em nuvem/móveis/SaaS, integre os resultados às suas ferramentas SIEM ou SOAR e sempre faça uma nova varredura após a correção para validar o fechamento.
Erros comuns Executar uma varredura única, ignorar dispositivos em nuvem ou BYOD, ignorar as credenciais de administrador (o que limita a visibilidade) e não validar a correção são erros frequentes. Esses erros deixam as organizações expostas, apesar de terem "escaneado" seus ativos.
Digitalização para aplicativo
O que a verificação de aplicativos detecta?
Software instalado, aplicativos ocultos ou não autorizados, versões antigas, vulnerabilidades e indicadores de malware.
É seguro fazer a varredura dos sistemas de produção?
Sim, desde que a varredura seja agendada adequadamente, use métodos não intrusivos e tenha as permissões de acesso adequadas.
Com que frequência você deve fazer o escaneamento?
Pelo menos mensalmas muitas organizações usam diariamente ou em tempo real digitalização.
A varredura de aplicativos é diferente da varredura de vulnerabilidades?
Sim .Varredura de aplicativos = descobrir softwareVarredura de vulnerabilidades = encontrar pontos fracos no software
Conclusão
Nas organizações modernas, os ecossistemas de software abrangem desktops locais, endpoints remotos, contêineres, cargas de trabalho na nuvem e plataformas SaaS, A "verificação de aplicativos" não é opcional, ela é fundamental. Um processo disciplinado e cíclico de planejamento, descoberta, detecção, geração de relatórios, correção e validação oferece visibilidade, reduz os riscos e apoia a conformidade. Se a sua estratégia de segurança inclui ferramentas como a Penligent para descoberta e correção automatizadas, você obtém uma vantagem poderosa: o inventário de software está sempre atualizado, as vulnerabilidades estão sempre visíveis e as ações de correção estão sempre em movimento.


